The information on this website is for general informational purposes only. Continuum GRC makes no representation or warranty, express or implied. Your use of the site is solely at your own risk. This site may contain links to third party content, which we do not warrant, endorse, or assume liability for.
Continuum GRC Survival Guidance - NIST 800-53
- Technical Writing Guidance
- Implementation Status
- Control Origination
- AC-1
- AC-2
- AC-2(1)
- AC-2(2)
- AC-2(3)
- AC-2(4)
- AC-2(5)
- AC-2(6)
- AC-2(7)
- AC-2(8)
- AC-2(9)
- AC-13
- AC-2(11)
- AC-2(12)
- AC-2(13)
- AC-3
- AC-14(1)
- AC-3(2)
- AC-3(3)
- AC-3(4)
- AC-3(5)
- AC-15
- AC-3(7)
- AC-3(8)
- AC-3(9)
- AC-3(10)
- AC-3(11)
- AC-3(12)
- AC-3(13)
- AC-3(14)
- AC-3(15)
- AC-4
- AC-4(1)
- AC-4(2)
- AC-4(3)
- AC-4(4)
- AC-4(5)
- AC-4(6)
- AC-4(7)
- AC-4(8)
- AC-4(9)
- AC-4(10)
- AC-4(11)
- AC-4(12)
- AC-4(13)
- AC-4(14)
- AC-4(15)
- AC-17(5)
- AC-4(17)
- AC-17(7)
- AC-4(19)
- AC-4(20)
- AC-4(21)
- AC-4(22)
- AC-4(23)
- AC-4(24)
- AC-4(25)
- AC-4(26)
- AC-4(27)
- AC-4(28)
- AC-4(29)
- AC-4(30)
- AC-4(31)
- AC-4(32)
- AC-5
- AC-6
- AC-6(1)
- AC-6(2)
- AC-6(3)
- AC-6(4)
- AC-6(5)
- AC-6(6)
- AC-6(7)
- AC-6(8)
- AC-6(9)
- AC-6(10)
- AC-7
- AC-17(8)
- AC-7(2)
- AC-7(3)
- AC-7(4)
- AC-8
- AC-9
- AC-9(1)
- AC-9(2)
- AC-9(3)
- AC-9(4)
- AC-10
- AC-11
- AC-11(1)
- AC-12
- AC-12(1)
- AC-12(2)
- AC-12(3)
- AC-18(2)
- AC-14
- AC-19(1)
- AC-19(2)
- AC-16
- AC-16(1)
- AC-16(2)
- AC-16(3)
- AC-16(4)
- AC-16(5)
- AC-16(6)
- AC-16(7)
- AC-16(8)
- AC-16(9)
- AC-16(10)
- AC-17
- AC-17(1)
- AC-17(2)
- AC-17(3)
- AC-17(4)
- AC-19(3)
- AC-17(6)
- AC-2(10)
- AC-3(1)
- AC-17(9)
- AC-17(10)
- AC-18
- AC-18(1)
- AC-3(6)
- AC-18(3)
- AC-18(4)
- AC-18(5)
- AC-19
- AC-4(16)
- AC-4(18)
- AC-7(1)
- AC-19(4)
- AC-19(5)
- AC-20
- AC-20(1)
- AC-20(2)
- AC-20(3)
- AC-20(4)
- AC-20(5)
- AC-21
- AC-21(1)
- AC-21(2)
- AC-22
- AC-23
- AC-24
- AC-24(1)
- AC-24(2)
- AC-25
- AT-1
- AT-2
- AT-2(1)
- AT-2(2)
- AT-2(3)
- AT-2(4)
- AT-2(5)
- AT-2(6)
- AT-3
- AT-3(1)
- AT-3(2)
- AT-3(3)
- AT-3(4)
- AT-3(5)
- AT-4
- AT-5
- AT-6
- AU-1
- AU-2
- AU-10(5)
- AU-14(2)
- AU-15
- AU-2(1)
- AU-3
- AU-3(1)
- AU-2(2)
- AU-3(3)
- AU-4
- AU-4(1)
- AU-5
- AU-5(1)
- AU-5(2)
- AU-5(3)
- AU-5(4)
- AU-5(5)
- AU-6
- AU-6(1)
- AU-2(3)
- AU-6(3)
- AU-6(4)
- AU-6(5)
- AU-6(6)
- AU-6(7)
- AU-6(8)
- AU-6(9)
- AU-2(4)
- AU-7
- AU-7(1)
- AU-3(2)
- AU-8
- AU-6(10)
- AU-6(2)
- AU-9
- AU-9(1)
- AU-9(2)
- AU-9(3)
- AU-9(4)
- AU-9(5)
- AU-9(6)
- AU-9(7)
- AU-10
- AU-10(1)
- AU-10(2)
- AU-10(3)
- AU-10(4)
- AU-7(2)
- AU-11
- AU-11(1)
- AU-12
- AU-12(1)
- AU-12(2)
- AU-12(3)
- AU-12(4)
- AU-13
- AU-13(1)
- AU-13(2)
- AU-13(3)
- AU-14
- AU-14(1)
- AU-8(1)
- AU-14(3)
- AU-8(2)
- AU-16
- AU-16(1)
- AU-16(2)
- AU-16(3)
- CA-1
- CA-2
- CA-2(1)
- CA-2(2)
- CA-2(3)
- CA-3
- CA-3(1)
- CA-3(2)
- CA-3(3)
- CA-3(4)
- CA-3(5)
- CA-3(6)
- CA-3(7)
- CA-4
- CA-5
- CA-5(1)
- CA-6
- CA-6(1)
- CA-6(2)
- CA-7
- CA-7(1)
- CA-7(2)
- CA-7(3)
- CA-7(4)
- CA-7(5)
- CA-7(6)
- CA-8
- CA-8(1)
- CA-8(2)
- CA-8(3)
- CA-9
- CA-9(1)
- CM-1
- CM-2
- CM-11(1)
- CM-2(2)
- CM-2(3)
- CM-2(1)
- CM-2(4)
- CM-2(6)
- CM-2(7)
- CM-3
- CM-3(1)
- CM-3(2)
- CM-3(3)
- CM-3(4)
- CM-3(5)
- CM-3(6)
- CM-3(7)
- CM-3(8)
- CM-4
- CM-4(1)
- CM-4(2)
- CM-5
- CM-5(1)
- CM-2(5)
- CM-5(2)
- CM-5(4)
- CM-5(5)
- CM-5(6)
- CM-5(3)
- CM-6
- CM-6(1)
- CM-6(2)
- CM-5(7)
- CM-6(3)
- CM-7
- CM-7(1)
- CM-7(2)
- CM-7(3)
- CM-7(4)
- CM-7(5)
- CM-7(6)
- CM-7(7)
- CM-7(8)
- CM-7(9)
- CM-8
- CM-8(1)
- CM-8(2)
- CM-8(3)
- CM-8(4)
- CM-6(4)
- CM-8(6)
- CM-8(7)
- CM-8(8)
- CM-8(9)
- CM-9
- CM-9(1)
- CM-10
- CM-10(1)
- CM-11
- CM-8(5)
- CM-11(2)
- CM-11(3)
- CM-12
- CM-12(1)
- CM-13
- CM-14
- CP-1
- CP-2
- CP-2(1)
- CP-2(2)
- CP-2(3)
- CP-10(1)
- CP-2(5)
- CP-2(6)
- CP-2(7)
- CP-2(8)
- CP-3
- CP-3(1)
- CP-3(2)
- CP-4
- CP-4(1)
- CP-4(2)
- CP-4(3)
- CP-4(4)
- CP-4(5)
- CP-10(3)
- CP-6
- CP-6(1)
- CP-6(2)
- CP-6(3)
- CP-7
- CP-7(1)
- CP-7(2)
- CP-7(3)
- CP-7(4)
- CP-10(5)
- CP-7(6)
- CP-8
- CP-8(1)
- CP-8(2)
- CP-8(3)
- CP-8(4)
- CP-8(5)
- CP-9
- CP-9(1)
- CP-9(2)
- CP-9(3)
- CP-2(4)
- CP-9(5)
- CP-9(6)
- CP-9(7)
- CP-9(8)
- CP-10
- CP-5
- CP-10(2)
- CP-7(5)
- CP-10(4)
- CP-9(4)
- CP-10(6)
- CP-11
- CP-12
- CP-13
- IA-1
- IA-2
- IA-2(1)
- IA-2(2)
- IA-2(11)
- IA-2(3)
- IA-2(5)
- IA-2(6)
- IA-2(4)
- IA-2(8)
- IA-2(7)
- IA-2(10)
- IA-2(9)
- IA-2(12)
- IA-2(13)
- IA-3
- IA-3(1)
- IA-3(2)
- IA-3(3)
- IA-3(4)
- IA-4
- IA-4(1)
- IA-4(2)
- IA-4(3)
- IA-4(4)
- IA-4(5)
- IA-4(6)
- IA-4(7)
- IA-4(8)
- IA-4(9)
- IA-5
- IA-5(1)
- IA-5(2)
- IA-5(11)
- IA-5(3)
- IA-5(5)
- IA-5(6)
- IA-5(7)
- IA-5(8)
- IA-5(9)
- IA-5(10)
- IA-5(4)
- IA-5(12)
- IA-5(13)
- IA-5(14)
- IA-5(15)
- IA-5(16)
- IA-5(17)
- IA-5(18)
- IA-6
- IA-7
- IA-8
- IA-8(1)
- IA-8(2)
- IA-8(3)
- IA-8(4)
- IA-8(5)
- IA-8(6)
- IA-9
- IA-9(1)
- IA-9(2)
- IA-10
- IA-11
- IA-12
- IA-12(1)
- IA-12(2)
- IA-12(3)
- IA-12(4)
- IA-12(5)
- IA-12(6)
- IR-1
- IR-2
- IR-2(1)
- IR-2(2)
- IR-2(3)
- IR-3
- IR-3(1)
- IR-3(2)
- IR-3(3)
- IR-4
- IR-4(1)
- IR-4(2)
- IR-4(3)
- IR-4(4)
- IR-4(5)
- IR-4(6)
- IR-4(7)
- IR-4(8)
- IR-4(9)
- IR-4(10)
- IR-4(11)
- IR-4(12)
- IR-4(13)
- IR-4(14)
- IR-4(15)
- IR-5
- IR-5(1)
- IR-6
- IR-6(1)
- IR-6(2)
- IR-6(3)
- IR-7
- IR-7(1)
- IR-7(2)
- IR-8
- IR-8(1)
- IR-9
- IR-10
- IR-9(2)
- IR-9(3)
- IR-9(4)
- IR-9(1)
- MA-1
- MA-2
- MA-2(1)
- MA-2(2)
- MA-3
- MA-3(1)
- MA-3(2)
- MA-3(3)
- MA-3(4)
- MA-3(5)
- MA-3(6)
- MA-4
- MA-4(1)
- MA-4(2)
- MA-4(3)
- MA-4(4)
- MA-4(5)
- MA-4(6)
- MA-4(7)
- MA-5
- MA-5(1)
- MA-5(2)
- MA-5(3)
- MA-5(4)
- MA-5(5)
- MA-6
- MA-6(1)
- MA-6(2)
- MA-6(3)
- MA-7
- MP-1
- MP-2
- MP-2(1)
- MP-2(2)
- MP-3
- MP-4
- MP-4(1)
- MP-4(2)
- MP-5
- MP-5(1)
- MP-5(2)
- MP-5(3)
- MP-5(4)
- MP-6
- MP-6(1)
- MP-6(2)
- MP-6(3)
- MP-6(4)
- MP-6(5)
- MP-6(6)
- MP-6(7)
- MP-6(8)
- MP-7
- MP-7(1)
- MP-7(2)
- MP-8
- MP-8(1)
- MP-8(2)
- MP-8(3)
- MP-8(4)
- PE-1
- PE-2
- PE-2(1)
- PE-2(2)
- PE-2(3)
- PE-3
- PE-3(1)
- PE-3(2)
- PE-3(3)
- PE-3(4)
- PE-3(5)
- PE-10(1)
- PE-3(7)
- PE-3(8)
- PE-4
- PE-5
- PE-13(3)
- PE-5(2)
- PE-18(1)
- PE-6
- PE-6(1)
- PE-6(2)
- PE-6(3)
- PE-6(4)
- PE-3(6)
- PE-8
- PE-8(1)
- PE-5(1)
- PE-8(3)
- PE-9
- PE-9(1)
- PE-9(2)
- PE-10
- PE-5(3)
- PE-11
- PE-11(1)
- PE-11(2)
- PE-12
- PE-12(1)
- PE-13
- PE-13(1)
- PE-13(2)
- PE-7
- PE-13(4)
- PE-14
- PE-14(1)
- PE-14(2)
- PE-15
- PE-15(1)
- PE-16
- PE-17
- PE-18
- PE-8(2)
- PE-19
- PE-19(1)
- PE-20
- PE-21
- PE-22
- PE-23
- PL-1
- PL-2
- PL-2(1)
- PL-2(2)
- PL-2(3)
- PL-3
- PL-4
- PL-4(1)
- PL-5
- PL-6
- PL-7
- PL-8
- PL-8(1)
- PL-8(2)
- PL-9
- PL-10
- PL-11
- PM-1
- PM-2
- PM-3
- PM-4
- PM-5
- PM-5(1)
- PM-6
- PM-7
- PM-7(1)
- PM-8
- PM-9
- PM-10
- PM-11
- PM-12
- PM-13
- PM-14
- PM-15
- PM-16
- PM-16(1)
- PM-17
- PM-18
- PM-19
- PM-20
- PM-20(1)
- PM-21
- PM-22
- PM-23
- PM-24
- PM-25
- PM-26
- PM-27
- PM-28
- PM-29
- PM-30
- PM-30(1)
- PM-31
- PM-32
- PS-1
- PS-2
- PS-3
- PS-3(1)
- PS-3(2)
- PS-3(3)
- PS-3(4)
- PS-4
- PS-4(1)
- PS-4(2)
- PS-5
- PS-6
- PS-6(1)
- PS-6(2)
- PS-6(3)
- PS-7
- PS-8
- PS-9
- PT-1
- PT-2
- PT-2(1)
- PT-2(2)
- PT-3
- PT-3(1)
- PT-3(2)
- PT-4
- PT-4(1)
- PT-4(2)
- PT-4(3)
- PT-5
- PT-5(1)
- PT-5(2)
- PT-6
- PT-6(1)
- PT-6(2)
- PT-7
- PT-7(1)
- PT-7(2)
- PT-8
- RA-1
- RA-2
- RA-2(1)
- RA-3
- RA-3(1)
- RA-3(2)
- RA-3(3)
- RA-3(4)
- RA-4
- RA-5
- RA-5(1)
- RA-5(2)
- RA-5(3)
- RA-5(4)
- RA-5(5)
- RA-5(6)
- RA-5(7)
- RA-5(8)
- RA-5(9)
- RA-5(10)
- RA-5(11)
- RA-6
- RA-7
- RA-8
- RA-9
- RA-10
- SA-1
- SA-2
- SA-3
- SA-3(1)
- SA-3(2)
- SA-3(3)
- SA-4
- SA-4(1)
- SA-4(2)
- SA-4(3)
- SA-12
- SA-4(5)
- SA-4(6)
- SA-4(7)
- SA-4(8)
- SA-4(9)
- SA-4(10)
- SA-4(11)
- SA-4(12)
- SA-5
- SA-12(1)
- SA-12(10)
- SA-12(11)
- SA-12(12)
- SA-12(13)
- SA-12(14)
- SA-12(15)
- SA-8
- SA-8(1)
- SA-8(2)
- SA-8(3)
- SA-8(4)
- SA-8(5)
- SA-8(6)
- SA-8(7)
- SA-8(8)
- SA-8(9)
- SA-8(10)
- SA-8(11)
- SA-8(12)
- SA-8(13)
- SA-8(14)
- SA-8(15)
- SA-8(16)
- SA-8(17)
- SA-8(18)
- SA-8(19)
- SA-8(20)
- SA-8(21)
- SA-8(22)
- SA-8(23)
- SA-8(24)
- SA-8(25)
- SA-8(26)
- SA-8(27)
- SA-8(28)
- SA-8(29)
- SA-8(30)
- SA-8(31)
- SA-8(32)
- SA-8(33)
- SA-9
- SA-9(1)
- SA-9(2)
- SA-9(3)
- SA-9(4)
- SA-9(5)
- SA-9(6)
- SA-9(7)
- SA-9(8)
- SA-10
- SA-10(1)
- SA-10(2)
- SA-10(3)
- SA-10(4)
- SA-10(5)
- SA-10(6)
- SA-10(7)
- SA-11
- SA-11(1)
- SA-11(2)
- SA-11(3)
- SA-11(4)
- SA-11(5)
- SA-11(6)
- SA-11(7)
- SA-11(8)
- SA-11(9)
- SA-12(2)
- SA-12(3)
- SA-12(4)
- SA-12(5)
- SA-12(6)
- SA-12(7)
- SA-12(8)
- SA-12(9)
- SA-13
- SA-14
- SA-14(1)
- SA-15(4)
- SA-15(9)
- SA-18
- SA-18(1)
- SA-18(2)
- SA-19
- SA-19(1)
- SA-19(2)
- SA-15
- SA-15(1)
- SA-15(2)
- SA-15(3)
- SA-19(3)
- SA-15(5)
- SA-15(6)
- SA-15(7)
- SA-15(8)
- SA-19(4)
- SA-15(10)
- SA-15(11)
- SA-15(12)
- SA-16
- SA-17
- SA-17(1)
- SA-17(2)
- SA-17(3)
- SA-17(4)
- SA-17(5)
- SA-17(6)
- SA-17(7)
- SA-17(8)
- SA-17(9)
- SA-21(1)
- SA-22(1)
- SA-4(4)
- SA-5(1)
- SA-5(2)
- SA-5(3)
- SA-5(4)
- SA-5(5)
- SA-20
- SA-21
- SA-6
- SA-22
- SA-7
- SA-23
- SC-1
- SC-2
- SC-2(1)
- SC-2(2)
- SC-3
- SC-3(1)
- SC-3(2)
- SC-3(3)
- SC-3(4)
- SC-3(5)
- SC-4
- SC-12(4)
- SC-4(2)
- SC-5
- SC-5(1)
- SC-5(2)
- SC-5(3)
- SC-6
- SC-7
- SC-12(5)
- SC-13(1)
- SC-7(3)
- SC-7(4)
- SC-7(5)
- SC-13(2)
- SC-7(7)
- SC-7(8)
- SC-7(9)
- SC-7(10)
- SC-7(11)
- SC-7(12)
- SC-7(13)
- SC-7(14)
- SC-7(15)
- SC-7(16)
- SC-7(17)
- SC-7(18)
- SC-7(19)
- SC-7(20)
- SC-7(21)
- SC-7(22)
- SC-7(23)
- SC-7(24)
- SC-7(25)
- SC-7(26)
- SC-7(27)
- SC-7(28)
- SC-7(29)
- SC-8
- SC-8(1)
- SC-8(2)
- SC-8(3)
- SC-8(4)
- SC-8(5)
- SC-13(3)
- SC-10
- SC-11
- SC-11(1)
- SC-12
- SC-12(1)
- SC-12(2)
- SC-12(3)
- SC-13(4)
- SC-14
- SC-12(6)
- SC-13
- SC-15(2)
- SC-19
- SC-20(1)
- SC-21(1)
- SC-23(2)
- SC-15
- SC-15(1)
- SC-23(4)
- SC-15(3)
- SC-15(4)
- SC-16
- SC-16(1)
- SC-16(2)
- SC-16(3)
- SC-17
- SC-18
- SC-18(1)
- SC-18(2)
- SC-18(3)
- SC-18(4)
- SC-18(5)
- SC-26(1)
- SC-20
- SC-30(1)
- SC-20(2)
- SC-21
- SC-33
- SC-22
- SC-23
- SC-23(1)
- SC-34(3)
- SC-23(3)
- SC-4(1)
- SC-23(5)
- SC-24
- SC-25
- SC-26
- SC-42(3)
- SC-27
- SC-28
- SC-28(1)
- SC-28(2)
- SC-28(3)
- SC-29
- SC-29(1)
- SC-30
- SC-7(1)
- SC-30(2)
- SC-30(3)
- SC-30(4)
- SC-30(5)
- SC-31
- SC-31(1)
- SC-31(2)
- SC-31(3)
- SC-32
- SC-32(1)
- SC-7(2)
- SC-34
- SC-34(1)
- SC-34(2)
- SC-7(6)
- SC-35
- SC-36
- SC-36(1)
- SC-36(2)
- SC-37
- SC-37(1)
- SC-38
- SC-39
- SC-39(1)
- SC-39(2)
- SC-40
- SC-40(1)
- SC-40(2)
- SC-40(3)
- SC-40(4)
- SC-41
- SC-42
- SC-42(1)
- SC-42(2)
- SC-9
- SC-42(4)
- SC-42(5)
- SC-43
- SC-44
- SC-45
- SC-45(1)
- SC-45(2)
- SC-46
- SC-47
- SC-48
- SC-48(1)
- SC-49
- SC-50
- SC-51
- SI-1
- SI-2
- SI-13(2)
- SI-2(2)
- SI-2(3)
- SI-2(4)
- SI-2(5)
- SI-2(6)
- SI-3
- SI-2(1)
- SI-3(1)
- SI-3(2)
- SI-3(4)
- SI-3(3)
- SI-3(6)
- SI-3(5)
- SI-3(8)
- SI-3(7)
- SI-3(10)
- SI-4
- SI-4(1)
- SI-4(2)
- SI-4(3)
- SI-4(4)
- SI-4(5)
- SI-3(9)
- SI-4(7)
- SI-4(6)
- SI-4(9)
- SI-4(10)
- SI-4(11)
- SI-4(12)
- SI-4(13)
- SI-4(14)
- SI-4(15)
- SI-4(16)
- SI-4(17)
- SI-4(18)
- SI-4(19)
- SI-4(20)
- SI-4(21)
- SI-4(22)
- SI-4(23)
- SI-4(24)
- SI-4(25)
- SI-5
- SI-5(1)
- SI-6
- SI-4(8)
- SI-6(2)
- SI-6(3)
- SI-7
- SI-7(1)
- SI-7(2)
- SI-7(3)
- SI-6(1)
- SI-7(5)
- SI-7(6)
- SI-7(7)
- SI-7(8)
- SI-7(9)
- SI-7(10)
- SI-7(11)
- SI-7(12)
- SI-7(13)
- SI-7(14)
- SI-7(15)
- SI-7(16)
- SI-7(17)
- SI-8
- SI-7(4)
- SI-8(2)
- SI-8(3)
- SI-8(1)
- SI-10
- SI-10(1)
- SI-10(2)
- SI-10(3)
- SI-10(4)
- SI-10(5)
- SI-10(6)
- SI-11
- SI-12
- SI-12(1)
- SI-12(2)
- SI-12(3)
- SI-13
- SI-13(1)
- SI-9
- SI-13(3)
- SI-13(4)
- SI-13(5)
- SI-14
- SI-14(1)
- SI-14(2)
- SI-14(3)
- SI-15
- SI-16
- SI-17
- SI-18
- SI-18(1)
- SI-18(2)
- SI-18(3)
- SI-18(4)
- SI-18(5)
- SI-19
- SI-19(1)
- SI-19(2)
- SI-19(3)
- SI-19(4)
- SI-19(5)
- SI-19(6)
- SI-19(7)
- SI-19(8)
- SI-20
- SI-21
- SI-22
- SI-23
- SR-1
- SR-2
- SR-2(1)
- SR-3
- SR-3(1)
- SR-3(2)
- SR-3(3)
- SR-4
- SR-4(1)
- SR-4(2)
- SR-4(3)
- SR-4(4)
- SR-5
- SR-5(1)
- SR-5(2)
- SR-6
- SR-6(1)
- SR-7
- SR-8
- SR-9
- SR-9(1)
- SR-10
- SR-11
- SR-11(1)
- SR-11(2)
- SR-11(3)
- SR-12
Technical Writing Guidance
Many of the general principles in writing a quality control implementation for document acceptance criteria are centered around the 4C’s … Clear, Concise, Consistent, and Complete. These will be the key points that your auditor will look for when you complete your security package.
- Clear - straightforward, avoiding convoluted phrases or over-long phrases;
- Concise - pack the most meaning into your words;
- Consistent - ensure terms have the same meaning throughout the document and items are referred to by the same name or description. The level of detail and presentation style should also remain the same throughout the document; and finally,
- Complete - be responsive to all applicable requirements and include all appropriate sections of the documentation.
Readability
- Refers to the Four Cs for text - Clear, Concise, Complete, and Consistent.
Is there a clear understanding of what was written?
Relevant
- Refers to the control implementation description addressing the specific control requirement(s), including any parameters.
Did the statement address the control requirement?
Sufficient
- Refers to the detail and thoroughness contained in the control implementation description; it should be sufficient to allow a reader to understand what is done and how it is done.
Is there enough detail to fully address all portions of the requirement, and to meet any security related needs?
Complete
- Refers to both the control implementation description’s agreement with the marked control template checkboxes and its consistency with other SSP text.
Do the implementation statements and the control template checkboxes match?
Implementation Status
Implementation Status is for indicating if one or more of the following for the system's operational status. If one or more of the Implemented, Partially implemented, Planned, Alternative implementation and Not applicable implementation status options are applicable.
If the system is under development or undergoing a major modification, provide information about the methods used to assure that up-front security requirements are included. Include specific controls in the appropriate sections of the plan depending on where the system is in the security life cycle.
In Continuum GRC, the following field is designed to document the Implementation Status.
Control Origination
Control Origination can be confusing. Get it wrong and your System Security Plan (SSP) control definitions will not be certifiable. This series of illustrations and explanations to guide you through Control Origination requirements present in all NIST and FISMA assessments, such as FedRAMP, CMMC, 800-53, HIPAA, CJIS, DFARS, 800-171, and others.
All controls originate from a system or from a business process. It is important to describe where the control originates from so that it is clear whose responsibility it is to implement, manage, and monitor the control. In some cases, the responsibility is shared by a CSP and by the customer. Use the definitions in the illustrations below to indicate where each security control originates from.
Throughout the SSP, policies and procedures must be explicitly referenced (title and date or version) so that it is clear which document is being referred to. Section numbers or similar mechanisms should allow the reviewer to easily find the reference.
For SaaS and PaaS systems that are inheriting controls from an IaaS (or anything lower in the stack), the “inherited” option in the SSP must be selected, and the implementation description must simply say “inherited.” Authorized reviewers will determine whether the control set is appropriate or not.
The NIST term "organization defined" must be interpreted as being the CSP's responsibility, unless otherwise indicated.
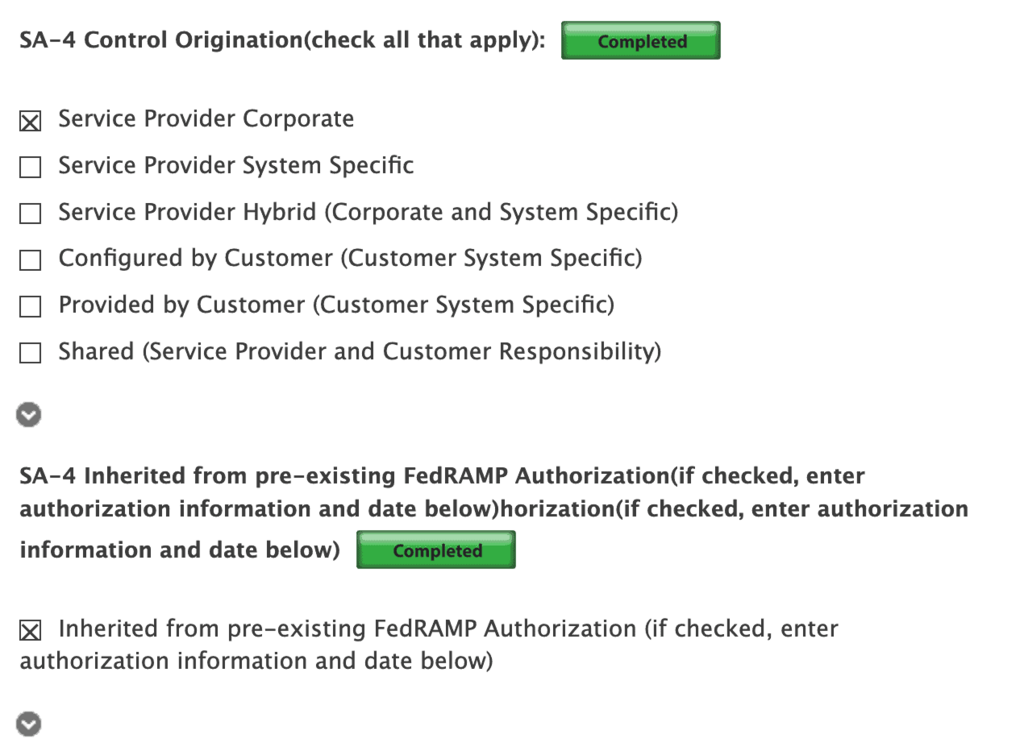
The official Control Origination classifications are:
- Service Provider Corporate
- Service Provider System Specific
- Service Provider Hybrid (Corporate and System Specific)
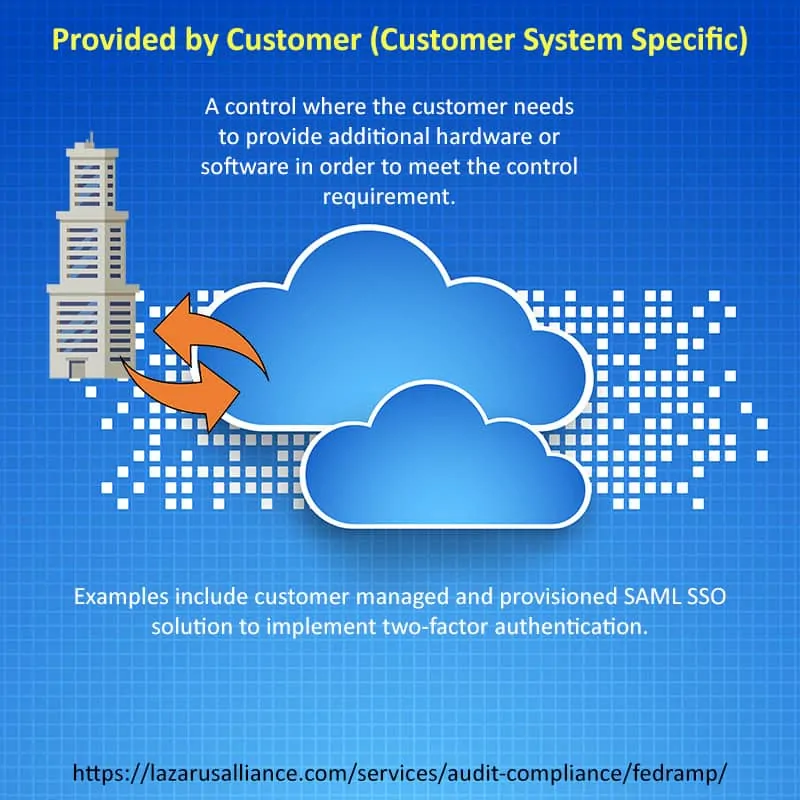
- Configured by Customer (Customer System Specific)
- Provided by Customer (Customer System Specific)
- Shared (Service Provider and Customer Responsibility)
- Inherited from pre-existing FedRAMP Authorization
The official Control Origination classifications are:
- Service Provider Corporate
- Service Provider System Specific
- Service Provider Hybrid (Corporate and System Specific)
- Configured by Customer (Customer System Specific)
- Provided by Customer (Customer System Specific)
- Shared (Service Provider and Customer Responsibility)
- Inherited from pre-existing FedRAMP Authorization
AC-1
"a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] access control policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
**Example: 'All users must authenticate with MFA before accessing sensitive systems'**
2. Procedures to facilitate the implementation of the access control policy and the associated access controls;
**Example: 'Quarterly review of user access rights by department managers'**
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the access control policy and procedures;
**Example: 'CISO designated as Access Control Policy Manager'**
c. Review and update the current access control:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
**Example: 'Annually and after major system changes'**
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]."
**Example: 'After new regulatory requirements or security incidents'**
AC-2
"a. Define and document the types of accounts allowed and specifically prohibited for use within the system;
**Example: 'Service accounts allowed, shared generic accounts prohibited'**
b. Assign account managers;
**Example: 'HR assigns user accounts, IT Security manages privileged accounts'**
c. Require [Assignment: organization-defined prerequisites and criteria] for group and role membership;
**Example: 'Manager approval + job role verification required'**
d. Specify:
1. Authorized users of the system;
**Example: 'Only employees with active HR status'**
2. Group and role membership; and
**Example: 'Finance group = accounting personnel only'**
3. Access authorizations (i.e., privileges) and [Assignment: organization-defined attributes (as required)] for each account;
**Example: 'Read-only for auditors, full access for system admins'**
e. Require approvals by [Assignment: organization-defined personnel or roles] for requests to create accounts;
**Example: 'Supervisor + Security team approval'**
f. Create, enable, modify, disable, and remove accounts in accordance with [Assignment: organization-defined policy, procedures, prerequisites, and criteria];
**Example: 'Accounts disabled after 90 days inactivity'**
g. Monitor the use of accounts;
**Example: 'Weekly review of privileged account activity'**
h. Notify account managers and [Assignment: organization-defined personnel or roles] within:
1. [Assignment: organization-defined time period] when accounts are no longer required;
**Example: 'Within 24 hours of project completion'**
2. [Assignment: organization-defined time period] when users are terminated or transferred; and
**Example: 'Within 1 hour of HR termination notice'**
3. [Assignment: organization-defined time period] when system usage or need-to-know changes for an individual;
**Example: 'Within 48 hours of role change'**
i. Authorize access to the system based on:
1. A valid access authorization;
2. Intended system usage; and
3. [Assignment: organization-defined attributes (as required)];
**Example: 'US citizenship required for classified systems'**
j. Review accounts for compliance with account management requirements [Assignment: organization-defined frequency];
**Example: 'Quarterly access review by data owners'**
k. Establish and implement a process for changing shared or group account authenticators (if deployed) when individuals are removed from the group; and
**Example: 'Immediate password change when team member leaves'**
l. Align account management processes with personnel termination and transfer processes."
**Example: 'Automated account disablement triggered by HR systems'**
AC-2(1)
Support the management of system accounts using [Assignment: organization-defined automated mechanisms].
**Example: 'Active Directory + automated provisioning tools'**
AC-2(2)
Automatically [Selection: remove; disable] temporary and emergency accounts after [Assignment: organization-defined time period for each type of account].
**Example: 'Emergency accounts auto-disabled after 72 hours'**
AC-2(3)
"Disable accounts within [Assignment: organization-defined time period] when the accounts:
(a) Have expired;
**Example: 'Contractor accounts disabled on contract end date'**
(b) Are no longer associated with a user or individual;
**Example: 'Orphaned accounts from incomplete offboarding'**
(c) Are in violation of organizational policy; or
**Example: 'Accounts with weak passwords'**
(d) Have been inactive for [Assignment: organization-defined time period]."
**Example: '90 days of inactivity'**
AC-2(4)
Automatically audit account creation, modification, enabling, disabling, and removal actions.
**Example: 'SIEM logs all Active Directory changes with before/after values'**
AC-2(5)
Require that users log out when [Assignment: organization-defined time period of expected inactivity or description of when to log out].
**Example: 'Auto-logout after 15 minutes of inactivity'**
AC-2(6)
Implement [Assignment: organization-defined dynamic privilege management capabilities].
**Example: 'Just-in-time elevation for specific tasks'**
AC-2(7)
"(a) Establish and administer privileged user accounts in accordance with [Selection: a role-based access scheme; an attribute-based access scheme];
**Example: 'Role-based: DBA role gets database admin privileges'**
(b) Monitor privileged role or attribute assignments;
**Example: 'Daily review of admin group membership'**
(c) Monitor changes to roles or attributes; and
**Example: 'Alert on privilege escalation attempts'**
(d) Revoke access when privileged role or attribute assignments are no longer appropriate."
**Example: 'Remove admin rights after project completion'**
AC-2(8)
Create, activate, manage, and deactivate [Assignment: organization-defined system accounts] dynamically.
**Example: 'CI/CD pipeline creates temporary service accounts'**
AC-2(9)
Only permit the use of shared and group accounts that meet [Assignment: organization-defined conditions for establishing shared and group accounts].
**Example: 'Only application service accounts, no user shared accounts'**
AC-13
[Withdrawn: Incorporated into AC-2 and AU-6.]
AC-2(11)
Enforce [Assignment: organization-defined circumstances and/or usage conditions] for [Assignment: organization-defined system accounts].
**Example: 'Database accounts only from approved IP ranges'**
AC-2(12)
"(a) Monitor system accounts for [Assignment: organization-defined atypical usage]; and
**Example: 'Login from unusual geographic location'**
(b) Report atypical usage of system accounts to [Assignment: organization-defined personnel or roles]."
**Example: 'Security Operations Center (SOC)'**
AC-2(13)
Disable accounts of individuals within [Assignment: organization-defined time period] of discovery of [Assignment: organization-defined significant risks].
**Example: 'Immediate disablement upon suspicion of compromise'**
AC-3
Enforce approved authorizations for logical access to information and system resources in accordance with applicable access control policies.
**Example: 'RBAC enforced by Active Directory group policy'**
AC-3(2)
Enforce dual authorization for [Assignment: organization-defined privileged commands and/or other organization-defined actions].
**Example: 'Two-person approval for production data deletion'**
AC-3(3)
"Enforce [Assignment: organization-defined mandatory access control policy] over the set of covered subjects and objects specified in the policy, and where the policy:
(a) Is uniformly enforced across the covered subjects and objects within the system;
**Example: 'SELinux mandatory access controls'**
(b) Specifies that a subject that has been granted access to information is constrained from doing any of the following;
(1) Passing the information to unauthorized subjects or objects;
**Example: 'No copy to unauthorized clearance level'**
(2) Granting its privileges to other subjects;
**Example: 'Cannot sudo to root'**
(3) Changing one or more security attributes (specified by the policy) on subjects, objects, the system, or system components;
**Example: 'Cannot change file classification labels'**
(4) Choosing the security attributes and attribute values (specified by the policy) to be associated with newly created or modified objects; and
**Example: 'New files inherit parent directory label'**
(5) Changing the rules governing access control; and
**Example: 'Cannot modify MAC policy'**
(c) Specifies that [Assignment: organization-defined subjects] may explicitly be granted [Assignment: organization-defined privileges] such that they are not limited by any defined subset (or all) of the above constraints."
**Example: 'System administrators granted full policy override'**
AC-3(4)
"Enforce [Assignment: organization-defined discretionary access control policy] over the set of covered subjects and objects specified in the policy, and where the policy specifies that a subject that has been granted access to information can do one or more of the following:
(a) Pass the information to any other subjects or objects;
**Example: 'File owner can share with anyone'**
(b) Grant its privileges to other subjects;
**Example: 'Can add others to file permissions'**
(c) Change security attributes on subjects, objects, the system, or the system's components;
**Example: 'Can modify file ACLs'**
(d) Choose the security attributes to be associated with newly created or revised objects; or
**Example: 'Can set permissions on new files'**
(e) Change the rules governing access control."
**Example: 'File owner can change ownership'**
AC-3(5)
Prevent access to [Assignment: organization-defined security-relevant information] except during secure, non-operable system states.
**Example: 'Crypto keys only accessible during FIPS validated boot'**
AC-15
[Withdrawn: Incorporated into MP-3.]
AC-3(7)
Enforce a role-based access control policy over defined subjects and objects and control access based upon [Assignment: organization-defined roles and users authorized to assume such roles].
**Example: 'Helpdesk role can reset passwords, cannot view account details'**
AC-3(8)
Enforce the revocation of access authorizations resulting from changes to the security attributes of subjects and objects based on [Assignment: organization-defined rules governing the timing of revocations of access authorizations].
**Example: 'Immediate revocation when clearance expires'**
AC-3(9)
"Release information outside of the system only if:
(a) The receiving [Assignment: organization-defined system or system component] provides [Assignment: organization-defined controls]; and
**Example: 'Receiving system must have FIPS 140-2 encryption'**
(b) [Assignment: organization-defined controls] are used to validate the appropriateness of the information designated for release."
**Example: 'DLP scan confirms no PII before transmission'**
AC-3(10)
Employ an audited override of automated access control mechanisms under [Assignment: organization-defined conditions] by [Assignment: organization-defined roles].
**Example: 'Emergency break-glass admin access with audit trail'**
AC-3(11)
Restrict access to data repositories containing [Assignment: organization-defined information types].
**Example: 'PCI cardholder data accessible only by payment team'**
AC-3(12)
"(a) Require applications to assert, as part of the installation process, the access needed to the following system applications and functions: [Assignment: organization-defined system applications and functions];
**Example: 'Web app declares need for database read/write access'**
(b) Provide an enforcement mechanism to prevent unauthorized access; and
**Example: 'AppArmor confinement enforces declared access'**
(c) Approve access changes after initial installation of the application."
**Example: 'Change control board approves access modifications'**
AC-3(13)
Enforce attribute-based access control policy over defined subjects and objects and control access based upon [Assignment: organization-defined attributes to assume access permissions].
**Example: 'Access granted if department=Finance AND clearance=Secret'**
AC-3(14)
Provide [Assignment: organization-defined mechanisms] to enable individuals to have access to the following elements of their personally identifiable information: [Assignment: organization-defined elements].
**Example: 'Self-service portal shows user's access rights'**
AC-3(15)
"(a) Enforce [Assignment: organization-defined mandatory access control policy] over the set of covered subjects and objects specified in the policy; and
**Example: 'SELinux for OS-level MAC'**
(b) Enforce [Assignment: organization-defined discretionary access control policy] over the set of covered subjects and objects specified in the policy."
**Example: 'POSIX ACLs for user file permissions'**
AC-4
Enforce approved authorizations for controlling the flow of information within the system and between connected systems based on [Assignment: organization-defined information flow control policies].
**Example: 'Firewall rules blocking HR data to Marketing VLAN'**
AC-4(1)
Use [Assignment: organization-defined security and privacy attributes] associated with [Assignment: organization-defined information, source, and destination objects] to enforce [Assignment: organization-defined information flow control policies] as a basis for flow control decisions.
**Example: 'Files tagged SECRET cannot flow to UNCLASSIFIED systems'**
AC-4(2)
Use protected processing domains to enforce [Assignment: organization-defined information flow control policies] as a basis for flow control decisions.
**Example: 'Air-gapped domains for classified processing'**
AC-4(3)
Enforce [Assignment: organization-defined information flow control policies].
**Example: 'Data Loss Prevention (DLP) gateway'**
AC-4(4)
Prevent encrypted information from bypassing [Assignment: organization-defined information flow control mechanisms] by [Selection (one or more): decrypting the information; blocking the flow of the encrypted information; terminating communications sessions attempting to pass encrypted information; [Assignment: organization-defined procedure or method]].
**Example: 'Decrypt and inspect HTTPS traffic at proxy'**
AC-4(5)
Enforce [Assignment: organization-defined limitations] on embedding data types within other data types.
**Example: 'Prohibit executables in PDF files'**
AC-4(6)
Enforce information flow control based on [Assignment: organization-defined metadata].
**Example: 'Block files without approved classification markings'**
AC-4(7)
Enforce one-way information flows through hardware-based flow control mechanisms.
**Example: 'Data diode from classified to unclassified network'**
AC-4(8)
"(a) Enforce information flow control using [Assignment: organization-defined security or privacy policy filters] as a basis for flow control decisions for [Assignment: organization-defined information flows]; and
**Example: 'Content filter blocks SSN patterns'**
(b) [Selection (one or more): Block; Strip; Modify; Quarantine] data after a filter processing failure in accordance with [Assignment: organization-defined security or privacy policy]."
**Example: 'Quarantine email attachments failing virus scan'**
AC-4(9)
Enforce the use of human reviews for [Assignment: organization-defined information flows] under the following conditions: [Assignment: organization-defined conditions].
**Example: 'Manual review for all TOP SECRET to SECRET downgrades'**
AC-4(10)
Provide the capability for privileged administrators to enable and disable [Assignment: organization-defined security or privacy policy filters] under the following conditions: [Assignment: organization-defined conditions].
**Example: 'Disable DLP during authorized penetration tests'**
AC-4(11)
Provide the capability for privileged administrators to configure [Assignment: organization-defined security or privacy policy filters] to support different security or privacy policies.
**Example: 'Different DLP rules for EU vs US employees'**
AC-4(12)
When transferring information between different security domains, use [Assignment: organization-defined data type identifiers] to validate data essential for information flow decisions.
**Example: 'XML schema validation for inter-domain transfers'**
AC-4(13)
When transferring information between different security domains, decompose information into [Assignment: organization-defined policy-relevant subcomponents] for submission to policy enforcement mechanisms.
**Example: 'Parse email into header/body/attachment for separate filtering'**
AC-4(14)
When transferring information between different security domains, implement [Assignment: organization-defined security or privacy policy filters] requiring fully enumerated formats that restrict data structure and content.
**Example: 'Only allow predefined XML schemas between domains'**
AC-4(15)
When transferring information between different security domains, examine the information for the presence of [Assignment: organization-defined unsanctioned information] and prohibit the transfer of such information in accordance with the [Assignment: organization-defined security or privacy policy].
**Example: 'Block hidden text or steganography in images'**
AC-17(5)
[Withdrawn: Incorporated into SI-4.]
AC-4(17)
Uniquely identify and authenticate source and destination points by [Selection (one or more): organization; system; application; service; individual] for information transfer.
**Example: 'Mutual TLS certificate authentication between services'**
AC-17(7)
[Withdrawn: Incorporated into AC-3(10).]
AC-4(19)
When transferring information between different security domains, implement [Assignment: organization-defined security or privacy policy filters] on metadata.
**Example: 'Validate file classification labels in metadata'**
AC-4(20)
Employ [Assignment: organization-defined solutions in approved configurations] to control the flow of [Assignment: organization-defined information] across security domains.
**Example: 'Approved cross-domain solution (CDS) hardware'**
AC-4(21)
Separate information flows logically or physically using [Assignment: organization-defined mechanisms and/or techniques] to accomplish [Assignment: organization-defined required separations by types of information].
**Example: 'Separate VLANs for PII vs public data'**
AC-4(22)
Provide access from a single device to computing platforms, applications, or data residing in multiple different security domains, while preventing information flow between the different security domains.
**Example: 'Thin client with domain isolation'**
AC-4(23)
When transferring information between different security domains, modify non-releasable information by implementing [Assignment: organization-defined modification action].
**Example: 'Redact SSN before sending to vendor'**
AC-4(24)
When transferring information between different security domains, parse incoming data into an internal normalized format and regenerate the data to be consistent with its intended specification.
**Example: 'Rebuild PDF from content stream to remove hidden data'**
AC-4(25)
When transferring information between different security domains, sanitize data to minimize [Selection (one or more): delivery of malicious content, command and control of malicious code, malicious code augmentation, and steganography encoded data; spillage of sensitive information] in accordance with [Assignment: organization-defined policy].
**Example: 'Remove all macros and embedded objects from Office files'**
AC-4(26)
When transferring information between different security domains, record and audit content filtering actions and results for the information being filtered.
**Example: 'Log all DLP blocking/quarantine decisions'**
AC-4(27)
When transferring information between different security domains, implement content filtering solutions that provide redundant and independent filtering mechanisms for each data type.
**Example: 'Multiple AV engines + sandbox analysis'**
AC-4(28)
When transferring information between different security domains, implement a linear content filter pipeline that is enforced with discretionary and mandatory access controls.
**Example: 'AV → DLP → Malware sandbox → Content validation'**
AC-4(29)
"When transferring information between different security domains, employ content filter orchestration engines to ensure that:
(a) Content filtering mechanisms successfully complete execution without errors; and
**Example: 'Fail closed if any filter stage fails'**
(b) Content filtering actions occur in the correct order and comply with [Assignment: organization-defined policy]."
**Example: 'Mandatory sequence: AV → DLP → Format validation'**
AC-4(30)
When transferring information between different security domains, implement content filtering mechanisms using multiple processes.
**Example: 'Separate processes for each filter type'**
AC-4(31)
When transferring information between different security domains, prevent the transfer of failed content to the receiving domain.
**Example: 'Drop packets failing any filter stage'**
AC-4(32)
"When transferring information between different security domains, the process that transfers information between filter pipelines:
(a) Does not filter message content;
**Example: 'Transport layer only validates metadata'**
(b) Validates filtering metadata;
**Example: 'Checks digital signature on filter results'**
(c) Ensures the content associated with the filtering metadata has successfully completed filtering; and
**Example: 'Verifies all filter stages passed'**
(d) Transfers the content to the destination filter pipeline."
**Example: 'Moves to next filter stage or final delivery'**
AC-5
"a. Identify and document [Assignment: organization-defined duties of individuals requiring separation]; and
**Example: 'Different people authorize and execute wire transfers'**
b. Define system access authorizations to support separation of duties."
**Example: 'Approver role cannot execute payments'**
AC-6
Employ the principle of least privilege, allowing only authorized accesses for users (or processes acting on behalf of users) that are necessary to accomplish assigned organizational tasks.
**Example: 'Developers get read-only prod DB access'**
AC-6(1)
"Authorize access for [Assignment: organization-defined individuals or roles] to:
(a) [Assignment: organization-defined security functions (deployed in hardware, software, and firmware)]; and
**Example: 'Security admins only access SIEM configuration'**
(b) [Assignment: organization-defined security-relevant information]."
**Example: 'Only auditors view security logs'**
AC-6(2)
Require that users of system accounts (or roles) with access to [Assignment: organization-defined security functions or security-relevant information] use non-privileged accounts or roles, when accessing nonsecurity functions.
**Example: 'Sysadmins use regular accounts for email'**
AC-6(3)
Authorize network access to [Assignment: organization-defined privileged commands] only for [Assignment: organization-defined compelling operational needs] and document the rationale for such access in the security plan for the system.
**Example: 'SSH jump host for emergency server access'**
AC-6(4)
Provide separate processing domains to enable finer-grained allocation of user privileges.
**Example: 'Containers with different privilege levels'**
AC-6(5)
Restrict privileged accounts on the system to [Assignment: organization-defined personnel or roles].
**Example: 'Only 5 designated sysadmins have root access'**
AC-6(6)
Prohibit privileged access to the system by non-organizational users.
**Example: 'No contractor root access allowed'**
AC-6(7)
"(a) Review [Assignment: organization-defined frequency] the privileges assigned to [Assignment: organization-defined roles or classes of users] to validate the need for such privileges; and
**Example: 'Monthly review of admin group membership'**
(b) Reassign or remove privileges, if necessary, to correctly reflect organizational mission and business needs."
**Example: 'Remove ex-employee admin rights'**
AC-6(8)
Prevent the following software from executing at higher privilege levels than users executing the software: [Assignment: organization-defined software].
**Example: 'Browsers cannot escalate beyond user privileges'**
AC-6(9)
Log the execution of privileged functions.
**Example: 'Audit all sudo commands'**
AC-6(10)
Prevent non-privileged users from executing privileged functions.
**Example: 'No privilege escalation without authorization'**
AC-7
"a. Enforce a limit of [Assignment: organization-defined number] consecutive invalid logon attempts by a user during a [Assignment: organization-defined time period]; and
**Example: '5 failed attempts in 15 minutes'**
b. Automatically [Selection (one or more): lock the account or node for an [Assignment: organization-defined time period]; lock the account or node until released by an administrator; delay next logon prompt per [Assignment: organization-defined delay algorithm]; notify system administrator; take other [Assignment: organization-defined action]] when the maximum number of unsuccessful attempts is exceeded."
**Example: 'Lock account for 30 minutes'**
AC-17(8)
[Withdrawn: Incorporated into CM-7.]
AC-7(2)
Purge or wipe information from [Assignment: organization-defined mobile devices] based on [Assignment: organization-defined purging or wiping requirements and techniques] after [Assignment: organization-defined number] consecutive, unsuccessful device logon attempts.
**Example: '10 failed PIN attempts wipes corporate phone'**
AC-7(3)
Limit the number of unsuccessful biometric logon attempts to [Assignment: organization-defined number].
**Example: '5 failed fingerprint attempts falls back to PIN'**
AC-7(4)
"(a) Allow the use of [Assignment: organization-defined authentication factors] that are different from the primary authentication factors after the number of organization-defined consecutive invalid logon attempts have been exceeded; and
**Example: 'Fallback to hardware token after password lockout'**
(b) Enforce a limit of [Assignment: organization-defined number] consecutive invalid logon attempts through use of the alternative factors by a user during a [Assignment: organization-defined time period]."
**Example: '3 failed token attempts locks account'**
AC-8
"a. Display [Assignment: organization-defined system use notification message or banner] to users before granting access to the system that provides privacy and security notices consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines and state that:
1. Users are accessing a U.S. Government system;
2. System usage may be monitored, recorded, and subject to audit;
3. Unauthorized use of the system is prohibited and subject to criminal and civil penalties; and
4. Use of the system indicates consent to monitoring and recording;
**Example: Standard DoD login banner**
b. Retain the notification message or banner on the screen until users acknowledge the usage conditions and take explicit actions to log on to or further access the system; and
**Example: 'Click "Accept" to continue'**
c. For publicly accessible systems:
1. Display system use information [Assignment: organization-defined conditions], before granting further access to the publicly accessible system;
**Example: 'Public WiFi terms of service'**
2. Display references, if any, to monitoring, recording, or auditing that are consistent with privacy accommodations for such systems that generally prohibit those activities; and
**Example: 'No monitoring on public guest network'**
3. Include a description of the authorized uses of the system."
**Example: 'Internet access only, no file sharing'**
AC-9
Notify the user, upon successful logon to the system, of the date and time of the last logon.
**Example: 'Last login: Oct 15, 2025 14:23 PM'**
AC-9(1)
Notify the user, upon successful logon, of the number of unsuccessful logon attempts since the last successful logon.
**Example: '3 failed login attempts since last access'**
AC-9(2)
Notify the user, upon successful logon, of the number of [Selection: successful logons; unsuccessful logon attempts; both] during [Assignment: organization-defined time period].
**Example: '2 logins from unusual location this week'**
AC-9(3)
Notify the user, upon successful logon, of changes to [Assignment: organization-defined security-related characteristics or parameters of the user's account] during [Assignment: organization-defined time period].
**Example: 'Your MFA device was recently changed'**
AC-9(4)
Notify the user, upon successful logon, of the following additional information: [Assignment: organization-defined additional information].
**Example: 'Security awareness training overdue'**
AC-10
Limit the number of concurrent sessions for each [Assignment: organization-defined account and/or account type] to [Assignment: organization-defined number].
**Example: '2 concurrent sessions per user account'**
AC-11
"a. Prevent further access to the system by [Selection (one or more): initiating a device lock after [Assignment: organization-defined time period] of inactivity; requiring the user to initiate a device lock before leaving the system unattended]; and
**Example: '15-minute screen lock timeout'**
b. Retain the device lock until the user reestablishes access using established identification and authentication procedures."
**Example: 'Requires password/PIN to unlock'**
AC-11(1)
Conceal, via the device lock, information previously visible on the display with a publicly viewable image.
**Example: 'Lock screen shows only company logo'**
AC-12
Automatically terminate a user session after [Assignment: organization-defined conditions or trigger events requiring session disconnect].
**Example: 'Session timeout after 30 minutes inactivity'**
AC-12(1)
Provide a logout capability for user-initiated communications sessions whenever authentication is used to gain access to [Assignment: organization-defined information resources].
**Example: 'Logout button on all web applications'**
AC-12(2)
Display an explicit logout message to users indicating the termination of authenticated communications sessions.
**Example: 'You have been logged out successfully'**
AC-12(3)
Display an explicit message to users indicating that the session will end in [Assignment: organization-defined time until end of session].
**Example: 'Session expires in 5 minutes'**
AC-18(2)
[Withdrawn: Incorporated into SI-4.]
AC-14
"a. Identify [Assignment: organization-defined user actions] that can be performed on the system without identification or authentication consistent with organizational mission and business functions; and
**Example: 'View public website content'**
b. Document and provide supporting rationale in the security plan for the system, user actions not requiring identification or authentication."
**Example: 'Anonymous access justified for marketing site'**
AC-19(1)
[Withdrawn: Incorporated into MP-7.]
AC-19(2)
[Withdrawn: Incorporated into MP-7.]
AC-16
"a. Provide the means to associate [Assignment: organization-defined types of security and privacy attributes] with [Assignment: organization-defined security and privacy attribute values] for information in storage, in process, and/or in transmission;
**Example: 'Classification: SECRET, Owner: Finance Dept'**
b. Ensure that the attribute associations are made and retained with the information;
**Example: 'Extended file attributes preserved'**
c. Establish the following permitted security and privacy attributes from the attributes defined in AC-16a for [Assignment: organization-defined systems]: [Assignment: organization-defined security and privacy attributes];
**Example: 'Classification, Caveat, Dissemination Controls'**
d. Determine the following permitted attribute values or ranges for each of the established attributes: [Assignment: organization-defined attribute values or ranges for established attributes];
**Example: 'UNCLASS, CONFIDENTIAL, SECRET, TOP SECRET'**
e. Audit changes to attributes; and
**Example: 'Log all classification label modifications'**
f. Review [Assignment: organization-defined security and privacy attributes] for applicability [Assignment: organization-defined frequency]."
**Example: 'Annual review of attribute definitions'**
AC-16(1)
Dynamically associate security and privacy attributes with [Assignment: organization-defined subjects and objects] in accordance with the following security and privacy policies as information is created and combined: [Assignment: organization-defined security and privacy policies].
**Example: 'New file inherits folder classification'**
AC-16(2)
Provide authorized individuals (or processes acting on behalf of individuals) the capability to define or change the value of associated security and privacy attributes.
**Example: 'Data owners can set sensitivity labels'**
AC-16(3)
Maintain the association and integrity of [Assignment: organization-defined security and privacy attributes] to [Assignment: organization-defined subjects and objects].
**Example: 'Cryptographic signing of metadata'**
AC-16(4)
Provide the capability to associate [Assignment: organization-defined security and privacy attributes] with [Assignment: organization-defined subjects and objects] by authorized individuals (or processes acting on behalf of individuals).
**Example: 'Classification officer GUI for labeling'**
AC-16(5)
Display security and privacy attributes in human-readable form on each object that the system transmits to output devices to identify [Assignment: organization-defined special dissemination, handling, or distribution instructions] using [Assignment: organization-defined human-readable, standard naming conventions].
**Example: '(C) CONFIDENTIAL // NOFORN'**
AC-16(6)
Require personnel to associate and maintain the association of [Assignment: organization-defined security and privacy attributes] with [Assignment: organization-defined subjects and objects] in accordance with [Assignment: organization-defined security and privacy policies].
**Example: 'Mandatory labeling training for all users'**
AC-16(7)
Provide a consistent interpretation of security and privacy attributes transmitted between distributed system components.
**Example: 'Standardized label format across all enclaves'**
AC-16(8)
Implement [Assignment: organization-defined techniques and technologies] in associating security and privacy attributes to information.
**Example: 'XATTR extended attributes on Linux filesystems'**
AC-16(9)
Change security and privacy attributes associated with information only via regrading mechanisms validated using [Assignment: organization-defined techniques or procedures].
**Example: 'Two-person rule for classification changes'**
AC-16(10)
Provide authorized individuals the capability to define or change the type and value of security and privacy attributes available for association with subjects and objects.
**Example: 'Security manager adds new caveat codes'**
AC-17
"a. Establish and document usage restrictions, configuration/connection requirements, and implementation guidance for each type of remote access allowed; and
**Example: 'VPN required, no direct RDP allowed'**
b. Authorize each type of remote access to the system prior to allowing such connections."
**Example: 'AO approves VPN client configuration'**
AC-17(1)
Employ automated mechanisms to monitor and control remote access methods.
**Example: 'NAC validates endpoint before VPN grant'**
AC-17(2)
Implement cryptographic mechanisms to protect the confidentiality and integrity of remote access sessions.
**Example: 'IPsec VPN with AES-256 encryption'**
AC-17(3)
Route remote accesses through authorized and managed network access control points.
**Example: 'All VPN traffic through two-factor gateway'**
AC-17(4)
"(a) Authorize the execution of privileged commands and access to security-relevant information via remote access only in a format that provides assessable evidence and for the following needs: [Assignment: organization-defined needs]; and
**Example: 'Emergency database recovery only'**
(b) Document the rationale for remote access in the security plan for the system."
**Example: 'Justified for DR/BCP requirements'**
AC-19(3)
[Withdrawn: Incorporated into MP-7.]
AC-17(6)
Protect information about remote access mechanisms from unauthorized use and disclosure.
**Example: 'VPN configuration files encrypted at rest'**
AC-2(10)
[Withdrawn: Incorporated into AC-2k.]
AC-3(1)
[Withdrawn: Incorporated into AC-6.]
AC-17(9)
Provide the capability to disconnect or disable remote access to the system within [Assignment: organization-defined time period].
**Example: 'Emergency VPN kill switch'**
AC-17(10)
Implement [Assignment: organization-defined mechanisms] to authenticate [Assignment: organization-defined remote commands].
**Example: 'Signed SSH commands from bastion host'**
AC-18
"a. Establish configuration requirements, connection requirements, and implementation guidance for each type of wireless access; and
**Example: 'WPA3-Enterprise with certificate auth only'**
b. Authorize each type of wireless access to the system prior to allowing such connections."
**Example: 'Only approved APs in authorized locations'**
AC-18(1)
Protect wireless access to the system using authentication of [Selection (one or more): users; devices] and encryption.
**Example: '802.1X + WPA3 with device certificates'**
AC-3(6)
[Withdrawn: Incorporated into MP-4 and SC-28.]
AC-18(3)
Disable, when not intended for use, wireless networking capabilities embedded within system components prior to issuance and deployment.
**Example: 'Disable WiFi chip in servers via BIOS'**
AC-18(4)
Identify and explicitly authorize users allowed to independently configure wireless networking capabilities.
**Example: 'Only Network team can configure APs'**
AC-18(5)
Select radio antennas and calibrate transmission power levels to reduce the probability that signals from wireless access points can be received outside of organization-controlled boundaries.
**Example: 'Low-power APs with directional antennas'**
AC-19
"a. Establish configuration requirements, connection requirements, and implementation guidance for organization-controlled mobile devices, to include when such devices are outside of controlled areas; and
**Example: 'Mobile Device Management (MDM) policy'**
b. Authorize the connection of mobile devices to organizational systems."
**Example: 'Only approved device models allowed'**
AC-4(16)
[Withdrawn: Incorporated into AC-4.]
AC-4(18)
[Withdrawn: Incorporated into AC-16.]
AC-7(1)
[Withdrawn: Incorporated into AC-7.]
AC-19(4)
"(a) Prohibit the use of unclassified mobile devices in facilities containing systems processing, storing, or transmitting classified information unless specifically permitted by the authorizing official; and
**Example: 'No personal phones in SCIF'**
(b) Enforce the following restrictions on individuals permitted by the authorizing official to use unclassified mobile devices in facilities containing systems processing, storing, or transmitting classified information:
(1) Connection of unclassified mobile devices to classified systems is prohibited;
**Example: 'No Bluetooth/USB to classified workstations'**
(2) Connection of unclassified mobile devices to unclassified systems requires approval from the authorizing official;
**Example: 'Approved guest WiFi only'**
(3) Use of internal or external modems or wireless interfaces within the unclassified mobile devices is prohibited; and
**Example: 'Airplane mode required in SCIF'**
(4) Unclassified mobile devices and the information stored on those devices are subject to random reviews and inspections by [Assignment: organization-defined security officials], and if classified information is found, the incident handling policy is followed.
**Example: 'Random phone inspections at SCIF entrance'**
(c) Restrict the connection of classified mobile devices to classified systems in accordance with [Assignment: organization-defined security policies]."
**Example: 'Two-person integrity for classified smartphones'**
AC-19(5)
Employ [Selection: full-device encryption; container-based encryption] to protect the confidentiality and integrity of information on [Assignment: organization-defined mobile devices].
**Example: 'BitLocker full disk encryption on laptops'**
AC-20
"a. [Selection (one or more): Establish [Assignment: organization-defined terms and conditions]; Identify [Assignment: organization-defined controls asserted to be implemented on external systems]], consistent with the trust relationships established with other organizations owning, operating, and/or maintaining external systems, allowing authorized individuals to:
1. Access the system from external systems; and
**Example: 'Work from home on personal laptop'**
2. Process, store, or transmit organization-controlled information using external systems; or
**Example: 'Cloud collaboration with partners'**
b. Prohibit the use of [Assignment: organizationally-defined types of external systems]."
**Example: 'No personal email for work documents'**
AC-20(1)
"Permit authorized individuals to use an external system to access the system or to process, store, or transmit organization-controlled information only after:
(a) Verification of the implementation of controls on the external system as specified in the organization's security and privacy policies and security and privacy plans; or
**Example: 'Annual vendor SOC 2 audit review'**
(b) Retention of approved system connection or processing agreements with the organizational entity hosting the external system."
**Example: 'Signed MOU with cloud provider'**
AC-20(2)
Restrict the use of organization-controlled portable storage devices by authorized individuals on external systems using [Assignment: organization-defined restrictions].
**Example: 'USB drives only work on corporate network'**
AC-20(3)
Restrict the use of non-organizationally owned systems or system components to process, store, or transmit organizational information using [Assignment: organization-defined restrictions].
**Example: 'BYOD requires MDM enrollment'**
AC-20(4)
Prohibit the use of [Assignment: organization-defined network accessible storage devices] in external systems.
**Example: 'No personal Dropbox for work files'**
AC-20(5)
Prohibit the use of organization-controlled portable storage devices by authorized individuals on external systems.
**Example: 'Corporate USB drives don't work off-network'**
AC-21
"a. Enable authorized users to determine whether access authorizations assigned to a sharing partner match the information's access and use restrictions for [Assignment: organization-defined information sharing circumstances where user discretion is required]; and
**Example: 'Warn if sharing SECRET with CONFIDENTIAL-cleared user'**
b. Employ [Assignment: organization-defined automated mechanisms or manual processes] to assist users in making information sharing and collaboration decisions."
**Example: 'Automated clearance checking in SharePoint'**
AC-21(1)
Employ [Assignment: organization-defined automated mechanisms] to enforce information-sharing decisions by authorized users based on access authorizations of sharing partners and access restrictions on information to be shared.
**Example: 'Block sharing if recipient lacks clearance'**
AC-21(2)
Implement information search and retrieval services that enforce [Assignment: organization-defined information sharing restrictions].
**Example: 'Search results filtered by user clearance'**
AC-22
"a. Designate individuals authorized to make information publicly accessible;
**Example: 'Only Communications team can post to public site'**
b. Train authorized individuals to ensure that publicly accessible information does not contain nonpublic information;
**Example: 'Annual public release training'**
c. Review the proposed content of information prior to posting onto the publicly accessible system to ensure that nonpublic information is not included; and
**Example: 'Two-person review before publishing'**
d. Review the content on the publicly accessible system for nonpublic information [Assignment: organization-defined frequency] and remove such information, if discovered."
**Example: 'Monthly web content scan for PII'**
AC-23
Employ [Assignment: organization-defined data mining prevention and detection techniques] for [Assignment: organization-defined data storage objects] to detect and protect against unauthorized data mining.
**Example: 'Query limits and anomaly detection in databases'**
AC-24
[Selection: Establish procedures; Implement mechanisms] to ensure [Assignment: organization-defined access control decisions] are applied to each access request prior to access enforcement.
**Example: 'Central policy decision point (PDP)'**
AC-24(1)
Transmit [Assignment: organization-defined access authorization information] using [Assignment: organization-defined controls] to [Assignment: organization-defined systems] that enforce access control decisions.
**Example: 'OAuth tokens distributed to microservices'**
AC-24(2)
Enforce access control decisions based on [Assignment: organization-defined security or privacy attributes] that do not include the identity of the user or process acting on behalf of the user.
**Example: 'Attribute-based access control (ABAC) using roles/time'**
AC-25
Implement a reference monitor for [Assignment: organization-defined access control policies] that is tamperproof, always invoked, and small enough to be subject to analysis and testing, the completeness of which can be assured.
**Example: 'SELinux policy enforcement kernel module'**
AT-1
"a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] awareness and training policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
**Example: 'Annual mandatory cybersecurity awareness training'**
2. Procedures to facilitate the implementation of the awareness and training policy and the associated awareness and training controls;
**Example: 'LMS tracking system for training completion'**
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the awareness and training policy and procedures; and
**Example: 'Chief Training Officer responsible'**
c. Review and update the current awareness and training:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
**Example: 'Annually and after major incidents'**
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]."
**Example: 'After new phishing campaigns'**
AT-2
"a. Provide security and privacy literacy training to system users (including managers, senior executives, and contractors):
1. As part of initial training for new users and [Assignment: organization-defined frequency] thereafter; and
**Example: 'Annual training for all users'**
2. When required by system changes or following [Assignment: organization-defined events];
**Example: 'After ransomware incident'**
b. Employ the following techniques to increase the security and privacy awareness of system users [Assignment: organization-defined awareness techniques];
**Example: 'Monthly phishing simulations'**
c. Update literacy training and awareness content [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
**Example: 'Quarterly content refresh'**
d. Incorporate lessons learned from internal or external security incidents or breaches into literacy training and awareness techniques."
**Example: 'Add SolarWinds lessons to training'**
AT-2(1)
Provide practical exercises in literacy training that simulate events and incidents.
**Example: 'Simulated phishing email campaign'**
AT-2(2)
Provide literacy training on recognizing and reporting potential indicators of insider threat.
**Example: 'Sudden large file downloads by coworker'**
AT-2(3)
Provide literacy training on recognizing and reporting potential and actual instances of social engineering and social mining.
**Example: 'USB drop attacks, pretext calling'**
AT-2(4)
Provide literacy training on recognizing suspicious communications and anomalous behavior in organizational systems using [Assignment: organization-defined indicators of malicious code].
**Example: 'Unexpected pop-ups, slow performance'**
AT-2(5)
Provide literacy training on the advanced persistent threat.
**Example: 'Nation-state actors with long dwell times'**
AT-2(6)
"(a) Provide literacy training on the cyber threat environment; and
**Example: 'Current ransomware groups targeting healthcare'**
(b) Reflect current cyber threat information in system operations."
**Example: 'Update IOCs in EDR systems'**
AT-3
"a. Provide role-based security and privacy training to personnel with the following roles and responsibilities: [Assignment: organization-defined roles and responsibilities]:
**Example: 'Sysadmins, DBAs, developers'**
1. Before authorizing access to the system, information, or performing assigned duties, and [Assignment: organization-defined frequency] thereafter; and
**Example: 'Annual recertification'**
2. When required by system changes;
**Example: 'New SIEM deployment training'**
b. Update role-based training content [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
**Example: 'After tool upgrades'**
c. Incorporate lessons learned from internal or external security incidents or breaches into role-based training."
**Example: 'Add Log4j vulnerability response training'**
AT-3(1)
Provide [Assignment: organization-defined personnel or roles] with initial and [Assignment: organization-defined frequency] training in the employment and operation of environmental controls.
**Example: 'Data center staff trained on HVAC failure response'**
AT-3(2)
Provide [Assignment: organization-defined personnel or roles] with initial and [Assignment: organization-defined frequency] training in the employment and operation of physical security controls.
**Example: 'Guards trained on badge reader troubleshooting'**
AT-3(3)
Provide practical exercises in security and privacy training that reinforce training objectives.
**Example: 'Tabletop exercise for incident response'**
AT-3(4)
[Withdrawn: Moved to AT-2(4).]
AT-3(5)
Provide [Assignment: organization-defined personnel or roles] with initial and [Assignment: organization-defined frequency] training in the employment and operation of personally identifiable information processing and transparency controls.
**Example: 'PII handlers trained on GDPR requirements'**
AT-4
"a. Document and monitor information security and privacy training activities, including security and privacy awareness training and specific role-based security and privacy training; and
**Example: 'LMS tracks completion dates and scores'**
b. Retain individual training records for [Assignment: organization-defined time period]."
**Example: '3 years after employee separation'**
AT-5
[Withdrawn: Incorporated into PM-15.]
AT-6
Provide feedback on organizational training results to the following personnel [Assignment: organization-defined frequency]: [Assignment: organization-defined personnel].
**Example: 'Quarterly phishing test results to managers'**
AU-1
"a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] audit and accountability policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
**Example: 'Log all privileged operations for 1 year'**
2. Procedures to facilitate the implementation of the audit and accountability policy and the associated audit and accountability controls;
**Example: 'SIEM configuration and log retention SOP'**
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the audit and accountability policy and procedures; and
**Example: 'Logging and Monitoring Manager'**
c. Review and update the current audit and accountability:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
**Example: 'Annually and after major incidents'**
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]."
**Example: 'After SIEM upgrade'**
AU-2
"a. Identify the types of events that the system is capable of logging in support of the audit function: [Assignment: organization-defined event types that the system is capable of logging];
**Example: 'Login failures, privilege use, file access'**
b. Coordinate the event logging function with other organizational entities requiring audit-related information to guide and inform the selection criteria for events to be logged;
**Example: 'Law enforcement input on forensic requirements'**
c. Specify the following event types for logging within the system: [Assignment: organization-defined event types (subset of the event types defined in AU-2a.) along with the frequency of (or situation requiring) logging for each identified event type];
**Example: 'All failed logins, privileged commands'**
d. Provide a rationale for why the event types selected for logging are deemed to be adequate to support after-the-fact investigations of incidents; and
**Example: 'Supports NIST IR playbook requirements'**
e. Review and update the event types selected for logging [Assignment: organization-defined frequency]."
**Example: 'Semi-annually'**
AU-10(5)
[Withdrawn: Incorporated into SI-7.]
AU-14(2)
[Withdrawn: Incorporated into AU-14.]
AU-15
[Withdrawn: Moved to AU-5(5).]
AU-2(1)
[Withdrawn: Incorporated into AU-12.]
AU-3
"Ensure that audit records contain information that establishes the following:
a. What type of event occurred;
**Example: 'File deletion'**
b. When the event occurred;
**Example: '2025-10-15 14:23:45 UTC'**
c. Where the event occurred;
**Example: 'Server DC01, share Finance'**
d. Source of the event;
**Example: 'User jdoe from IP 192.168.1.100'**
e. Outcome of the event; and
**Example: 'Success'**
f. Identity of any individuals, subjects, or objects/entities associated with the event."
**Example: 'File: budget_2025.xlsx'**
AU-3(1)
Generate audit records containing the following additional information: [Assignment: organization-defined additional information].
**Example: 'Parent process ID, command line arguments'**
AU-2(2)
[Withdrawn: Incorporated into AU-12.]
AU-3(3)
Limit personally identifiable information contained in audit records to the following elements identified in the privacy risk assessment: [Assignment: organization-defined elements].
**Example: 'Username only, mask full email address'**
AU-4
Allocate audit log storage capacity to accommodate [Assignment: organization-defined audit log retention requirements].
**Example: '90 days online, 1 year archival'**
AU-4(1)
Transfer audit logs [Assignment: organization-defined frequency] to a different system, system component, or media other than the system or system component conducting the logging.
**Example: 'Hourly syslog forwarding to central SIEM'**
AU-5
"a. Alert [Assignment: organization-defined personnel or roles] within [Assignment: organization-defined time period] in the event of an audit logging process failure; and
**Example: 'Page SOC within 5 minutes'**
b. Take the following additional actions: [Assignment: organization-defined additional actions]."
**Example: 'Halt system if logging cannot be restored'**
AU-5(1)
Provide a warning to [Assignment: organization-defined personnel, roles, and/or locations] within [Assignment: organization-defined time period] when allocated audit log storage volume reaches [Assignment: organization-defined percentage] of repository maximum audit log storage capacity.
**Example: 'Alert at 75% and 90% capacity'**
AU-5(2)
Provide an alert within [Assignment: organization-defined real-time period] to [Assignment: organization-defined personnel, roles, and/or locations] when the following audit failure events occur: [Assignment: organization-defined audit logging failure events requiring real-time alerts].
**Example: 'Immediate alert for syslog service crash'**
AU-5(3)
Enforce configurable network communications traffic volume thresholds reflecting limits on audit log storage capacity and [Selection: reject; delay] network traffic above those thresholds.
**Example: 'Drop syslog when SIEM storage full'**
AU-5(4)
Invoke a [Selection: full system shutdown; partial system shutdown; degraded operational mode with limited mission or business functionality available] in the event of [Assignment: organization-defined audit logging failures], unless an alternate audit logging capability exists.
**Example: 'Degraded mode if primary logging fails'**
AU-5(5)
Provide an alternate audit logging capability in the event of a failure in primary audit logging capability that implements [Assignment: organization-defined alternate audit logging functionality].
**Example: 'Local disk logging when network SIEM unreachable'**
AU-6
"a. Review and analyze system audit records [Assignment: organization-defined frequency] for indications of [Assignment: organization-defined inappropriate or unusual activity] and the potential impact of the inappropriate or unusual activity;
**Example: 'Daily SOC review for anomalies'**
b. Report findings to [Assignment: organization-defined personnel or roles]; and
**Example: 'Escalate high-severity alerts to IR team'**
c. Adjust the level of audit record review, analysis, and reporting within the system when there is a change in risk based on law enforcement information, intelligence information, or other credible sources of information."
**Example: 'Increase monitoring during election season'**
AU-6(1)
Integrate audit record review, analysis, and reporting processes using [Assignment: organization-defined automated mechanisms].
**Example: 'SIEM with correlation rules'**
AU-2(3)
[Withdrawn: Incorporated into AU-2.]
AU-6(3)
Analyze and correlate audit records across different repositories to gain organization-wide situational awareness.
**Example: 'Combine Windows, Linux, network logs in SIEM'**
AU-6(4)
Provide and implement the capability to centrally review and analyze audit records from multiple components within the system.
**Example: 'Unified SIEM dashboard'**
AU-6(5)
Integrate analysis of audit records with analysis of [Selection (one or more): vulnerability scanning information; performance data; system monitoring information; [Assignment: organization-defined data/information collected from other sources]] to further enhance the ability to identify inappropriate or unusual activity.
**Example: 'Correlate Nessus findings with login anomalies'**
AU-6(6)
Correlate information from audit records with information obtained from monitoring physical access to further enhance the ability to identify suspicious, inappropriate, unusual, or malevolent activity.
**Example: 'Badge swipe + VPN login correlation'**
AU-6(7)
Specify the permitted actions for each [Selection (one or more): system process; role; user] associated with the review, analysis, and reporting of audit record information.
**Example: 'Tier 1 analysts can view, Tier 3 can modify alerts'**
AU-6(8)
Perform a full text analysis of logged privileged commands in a physically distinct component or subsystem of the system, or other system that is dedicated to that analysis.
**Example: 'Separate analytics cluster for sudo logs'**
AU-6(9)
Correlate information from nontechnical sources with audit record information to enhance organization-wide situational awareness.
**Example: 'HR termination list + account activity'**
AU-2(4)
[Withdrawn: Incorporated into AC-6(9).]
AU-7
"Provide and implement an audit record reduction and report generation capability that:
a. Supports on-demand audit record review, analysis, and reporting requirements and after-the-fact investigations of incidents; and
**Example: 'Search failed logins by username'**
b. Does not alter the original content or time ordering of audit records."
**Example: 'Immutable raw log archive'**
AU-7(1)
Provide and implement the capability to process, sort, and search audit records for events of interest based on the following content: [Assignment: organization-defined fields within audit records].
**Example: 'Filter by source IP, user, event type'**
AU-3(2)
[Withdrawn: Incorporated into PL-9.]
AU-8
"a. Use internal system clocks to generate time stamps for audit records; and
**Example: 'NTP synchronized system clocks'**
b. Record time stamps for audit records that meet [Assignment: organization-defined granularity of time measurement] and that use Coordinated Universal Time, have a fixed local time offset from Coordinated Universal Time, or that include the local time offset as part of the time stamp."
**Example: 'Millisecond precision UTC+5:00'**
AU-6(10)
[Withdrawn: Incorporated into AU-6.]
AU-6(2)
[Withdrawn: Incorporated into SI-4.]
AU-9
"a. Protect audit information and audit logging tools from unauthorized access, modification, and deletion; and
**Example: 'SIEM logs encrypted at rest'**
b. Alert [Assignment: organization-defined personnel or roles] upon detection of unauthorized access, modification, or deletion of audit information."
**Example: 'Tamper detection alerts to SOC'**
AU-9(1)
Write audit trails to hardware-enforced, write-once media.
**Example: 'WORM optical drives for long-term retention'**
AU-9(2)
Store audit records [Assignment: organization-defined frequency] in a repository that is part of a physically different system or system component than the system or component being audited.
**Example: 'Daily transfer to separate log server'**
AU-9(3)
Implement cryptographic mechanisms to protect the integrity of audit information and audit tools.
**Example: 'SHA-256 hashes of log files'**
AU-9(4)
Authorize access to management of audit logging functionality to only [Assignment: organization-defined subset of privileged users or roles].
**Example: 'Only Logging Admin role'**
AU-9(5)
Enforce dual authorization for [Selection (one or more): movement; deletion] of [Assignment: organization-defined audit information].
**Example: 'Two-person rule for log archive deletion'**
AU-9(6)
Authorize read-only access to audit information to [Assignment: organization-defined subset of privileged users or roles].
**Example: 'Analysts read-only, admins full access'**
AU-9(7)
Store audit information on a component running a different operating system than the system or component being audited.
**Example: 'Linux SIEM for Windows endpoint logs'**
AU-10
Provide irrefutable evidence that an individual (or process acting on behalf of an individual) has performed [Assignment: organization-defined actions to be covered by non-repudiation].
**Example: 'Digitally signed approval workflows'**
AU-10(1)
"(a) Bind the identity of the information producer with the information to [Assignment: organization-defined strength of binding]; and
**Example: 'PKI digital signature'**
(b) Provide the means for authorized individuals to determine the identity of the producer of the information."
**Example: 'Signature validation shows jdoe signed document'**
AU-10(2)
"(a) Validate the binding of the information producer identity to the information at [Assignment: organization-defined frequency]; and
**Example: 'Daily CRL/OCSP checks'**
(b) Perform [Assignment: organization-defined actions] in the event of a validation error."
**Example: 'Quarantine invalidly signed files'**
AU-10(3)
Maintain reviewer or releaser credentials within the established chain of custody for information reviewed or released.
**Example: 'Document approval chain preserved'**
AU-10(4)
"(a) Validate the binding of the information reviewer identity to the information at the transfer or release points prior to release or transfer between [Assignment: organization-defined security domains]; and
**Example: 'Verify signature before cross-domain transfer'**
(b) Perform [Assignment: organization-defined actions] in the event of a validation error."
**Example: 'Reject transfer if signature invalid'**
AU-7(2)
[Withdrawn: Incorporated into AU-7(1).]
AU-11
Retain audit records for [Assignment: organization-defined time period consistent with records retention policy] to provide support for after-the-fact investigations of incidents and to meet regulatory and organizational information retention requirements.
**Example: '1 year hot, 7 years cold storage'**
AU-11(1)
Employ [Assignment: organization-defined measures] to ensure that long-term audit records generated by the system can be retrieved.
**Example: 'Log format migration every 5 years'**
AU-12
"a. Provide audit record generation capability for the event types the system is capable of auditing as defined in AU-2a on [Assignment: organization-defined system components];
**Example: 'All servers, workstations, network devices'**
b. Allow [Assignment: organization-defined personnel or roles] to select the event types that are to be logged by specific components of the system; and
**Example: 'Security team configures logging levels'**
c. Generate audit records for the event types defined in AU-2c that include the audit record content defined in AU-3."
**Example: 'Syslog format with all required fields'**
AU-12(1)
Compile audit records from [Assignment: organization-defined system components] into a system-wide (logical or physical) audit trail that is time-correlated to within [Assignment: organization-defined level of tolerance for the relationship between time stamps of individual records in the audit trail].
**Example: '1-second synchronization across all hosts'**
AU-12(2)
Produce a system-wide (logical or physical) audit trail composed of audit records in a standardized format.
**Example: 'All logs in CEF format'**
AU-12(3)
Provide and implement the capability for [Assignment: organization-defined individuals or roles] to change the logging to be performed on [Assignment: organization-defined system components] based on [Assignment: organization-defined selectable event criteria] within [Assignment: organization-defined time thresholds].
**Example: 'Real-time logging level changes during incident'**
AU-12(4)
Provide and implement the capability for auditing the parameters of user query events for data sets containing personally identifiable information.
**Example: 'Log all SQL queries against customer database'**
AU-13
"a. Monitor [Assignment: organization-defined open-source information and/or information sites] [Assignment: organization-defined frequency] for evidence of unauthorized disclosure of organizational information; and
**Example: 'Daily Google alerts for company name + SSN'**
b. If an information disclosure is discovered:
1. Notify [Assignment: organization-defined personnel or roles]; and
**Example: 'Alert IR team immediately'**
2. Take the following additional actions: [Assignment: organization-defined additional actions]."
**Example: 'Issue public statement if confirmed breach'**
AU-13(1)
Monitor open-source information and information sites using [Assignment: organization-defined automated mechanisms].
**Example: 'Commercial dark web monitoring service'**
AU-13(2)
Review the list of open-source information sites being monitored [Assignment: organization-defined frequency].
**Example: 'Monthly review of alert keywords'**
AU-13(3)
Employ discovery techniques, processes, and tools to determine if external entities are replicating organizational information in an unauthorized manner.
**Example: 'Digital watermark detection in documents'**
AU-14
"a. Provide and implement the capability for [Assignment: organization-defined users or roles] to [Selection (one or more): record; view; hear; log] the content of a user session under [Assignment: organization-defined circumstances]; and
**Example: 'Record admin sessions for compliance'**
b. Develop, integrate, and use session auditing activities in consultation with legal counsel and in accordance with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines."
**Example: 'Privacy impact assessment completed'**
AU-14(1)
Initiate session audits automatically at system start-up.
**Example: 'All privileged sessions auto-recorded'**
AU-8(1)
[Withdrawn: Moved to SC-45(1).]
AU-14(3)
Provide and implement the capability for authorized users to remotely view and hear content related to an established user session in real time.
**Example: 'Live session shadowing for helpdesk'**
AU-8(2)
[Withdrawn: Moved to SC-45(2).]
AU-16
Employ [Assignment: organization-defined methods] for coordinating [Assignment: organization-defined audit information] among external organizations when audit information is transmitted across organizational boundaries.
**Example: 'ISAC threat sharing with ISAO format'**
AU-16(1)
Preserve the identity of individuals in cross-organizational audit trails.
**Example: 'Pseudonymized user IDs in shared logs'**
AU-16(2)
Provide cross-organizational audit information to [Assignment: organization-defined organizations] based on [Assignment: organization-defined cross-organizational sharing agreements].
**Example: 'Share IOCs with sector ISAC members'**
AU-16(3)
Implement [Assignment: organization-defined measures] to disassociate individuals from audit information transmitted across organizational boundaries.
**Example: 'Hash usernames before sharing logs'**
Here is the NIST 800-53 CA-MA document with brief example descriptions inserted for each control requirement:
```html
CA-1
"a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] assessment, authorization, and monitoring policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
**Example: 'Annual ATO process with continuous monitoring'**
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
2. Procedures to facilitate the implementation of the assessment, authorization, and monitoring policy and the associated assessment, authorization, and monitoring controls;
**Example: 'SSP template and POA&M tracking process'**
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the assessment, authorization, and monitoring policy and procedures; and
**Example: 'AO designated as Authorization Official'**
c. Review and update the current assessment, authorization, and monitoring:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
**Example: 'Annually and after major incidents'**
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]."
**Example: 'After FISMA updates'**
CA-2
"a. Select the appropriate assessor or assessment team for the type of assessment to be conducted;
**Example: '3rd party for initial ATO, internal for annual'**
b. Develop a control assessment plan that describes the scope of the assessment including:
1. Controls and control enhancements under assessment;
**Example: 'All 325 controls + 50 enhancements'**
2. Assessment procedures to be used to determine control effectiveness; and
**Example: 'NIST 800-53A test procedures'**
3. Assessment environment, assessment team, and assessment roles and responsibilities;
**Example: 'Prod environment, 5 assessors, AO approves'**
c. Ensure the control assessment plan is reviewed and approved by the authorizing official or designated representative prior to conducting the assessment;
**Example: 'AO signs assessment plan'**
d. Assess the controls in the system and its environment of operation [Assignment: organization-defined frequency] to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting established security and privacy requirements;
**Example: 'Quarterly control assessments'**
e. Produce a control assessment report that document the results of the assessment; and
**Example: 'SAR with findings and evidence'**
f. Provide the results of the control assessment to [Assignment: organization-defined individuals or roles]."
**Example: 'AO, ISSM, and system owners'**
CA-2(1)
Employ independent assessors or assessment teams to conduct control assessments.
**Example: 'External C3PAO for FedRAMP assessment'**
CA-2(2)
Include as part of control assessments, [Assignment: organization-defined frequency], [Selection: announced; unannounced], [Selection (one or more): in-depth monitoring; security instrumentation; automated security test cases; vulnerability scanning; malicious user testing; insider threat assessment; performance and load testing; data leakage or data loss assessment; [Assignment: organization-defined other forms of assessment]].
**Example: 'Monthly vuln scans + quarterly red team'**
CA-2(3)
Leverage the results of control assessments performed by [Assignment: organization-defined external organization] on [Assignment: organization-defined system] when the assessment meets [Assignment: organization-defined requirements].
**Example: 'Use AWS FedRAMP ATO for cloud inheritance'**
CA-3
"a. Approve and manage the exchange of information between the system and other systems using [Selection (one or more): interconnection security agreements; information exchange security agreements; memoranda of understanding or agreement; service level agreements; user agreements; nondisclosure agreements; [Assignment: organization-defined type of agreement]];
**Example: 'MOU with partner agency for data sharing'**
b. Document, as part of each exchange agreement, the interface characteristics, security and privacy requirements, controls, and responsibilities for each system, and the impact level of the information communicated; and
**Example: 'API specs, FIPS 140-2 encryption, Moderate impact'**
c. Review and update the agreements [Assignment: organization-defined frequency]."
**Example: 'Annually and after system changes'**
CA-3(1)
[Withdrawn: Moved to SC-7(25).]
CA-3(2)
[Withdrawn: Moved to SC-7(26).]
CA-3(3)
[Withdrawn: Moved to SC-7(27).]
CA-3(4)
[Withdrawn: Moved to SC-7(28).]
CA-3(5)
[Withdrawn: Moved to SC-7(5).]
CA-3(6)
Verify that individuals or systems transferring data between interconnecting systems have the requisite authorizations (i.e., write permissions or privileges) prior to accepting such data.
**Example: 'Check sender clearance before accepting file transfer'**
CA-3(7)
"(a) Identify transitive (downstream) information exchanges with other systems through the systems identified in CA-3a; and
**Example: 'Map Partner → Vendor → Subcontractor flows'**
(b) Take measures to ensure that transitive (downstream) information exchanges cease when the controls on identified transitive (downstream) systems cannot be verified or validated."
**Example: 'Terminate vendor contract if audit fails'**
CA-4
[Withdrawn: Incorporated into CA-2.]
CA-5
"a. Develop a plan of action and milestones for the system to document the planned remediation actions of the organization to correct weaknesses or deficiencies noted during the assessment of the controls and to reduce or eliminate known vulnerabilities in the system; and
**Example: 'POA&M with 30/60/90 day remediation targets'**
b. Update existing plan of action and milestones [Assignment: organization-defined frequency] based on the findings from control assessments, independent audits or reviews, and continuous monitoring activities."
**Example: 'Monthly POA&M review meetings'**
CA-5(1)
Ensure the accuracy, currency, and availability of the plan of action and milestones for the system using [Assignment: organization-defined automated mechanisms].
**Example: 'CyberArk POA&M tracker dashboard'**
CA-6
"a. Assign a senior official as the authorizing official for the system;
**Example: 'Deputy CIO as AO'**
b. Assign a senior official as the authorizing official for common controls available for inheritance by organizational systems;
**Example: 'CISO authorizes enterprise logging controls'**
c. Ensure that the authorizing official for the system, before commencing operations:
1. Accepts the use of common controls inherited by the system; and
**Example: 'Sign common control inheritance memo'**
2. Authorizes the system to operate;
**Example: 'Sign ATO letter'**
d. Ensure that the authorizing official for common controls authorizes the use of those controls for inheritance by organizational systems;
**Example: 'Enterprise controls ATO'**
e. Update the authorizations [Assignment: organization-defined frequency]."
**Example: 'Annually or after significant changes'**
CA-6(1)
Employ a joint authorization process for the system that includes multiple authorizing officials from the same organization conducting the authorization.
**Example: 'Mission owner + security AO joint ATO'**
CA-6(2)
Employ a joint authorization process for the system that includes multiple authorizing officials with at least one authorizing official from an organization external to the organization conducting the authorization.
**Example: 'Agency + vendor joint cloud ATO'**
CA-7
"Develop a system-level continuous monitoring strategy and implement continuous monitoring in accordance with the organization-level continuous monitoring strategy that includes:
a. Establishing the following system-level metrics to be monitored: [Assignment: organization-defined system-level metrics];
**Example: 'Vuln scan results, log review coverage'**
b. Establishing [Assignment: organization-defined frequencies] for monitoring and [Assignment: organization-defined frequencies] for assessment of control effectiveness;
**Example: 'Daily logs, monthly control tests'**
c. Ongoing control assessments in accordance with the continuous monitoring strategy;
**Example: 'Automated control checks via SCAP'**
d. Ongoing monitoring of system and organization-defined metrics in accordance with the continuous monitoring strategy;
**Example: 'Splunk dashboards for key metrics'**
e. Correlation and analysis of information generated by control assessments and monitoring;
**Example: 'SIEM correlation rules'**
f. Response actions to address results of the analysis of control assessment and monitoring information; and
**Example: 'Auto-ticket creation for findings'**
g. Reporting the security and privacy status of the system to [Assignment: organization-defined personnel or roles] [Assignment: organization-defined frequency]."
**Example: 'Monthly OSCAL ConMon report to AO'**
CA-7(1)
Employ independent assessors or assessment teams to monitor the controls in the system on an ongoing basis.
**Example: 'Quarterly 3rd party ConMon validation'**
CA-7(2)
[Withdrawn: Incorporated into CA-2.]
CA-7(3)
Employ trend analyses to determine if control implementations, the frequency of continuous monitoring activities, and the types of activities used in the continuous monitoring process need to be modified based on empirical data.
**Example: 'Reduce scan frequency if zero vulns for 6 months'**
CA-7(4)
"Ensure risk monitoring is an integral part of the continuous monitoring strategy that includes the following:
(a) Effectiveness monitoring;
**Example: 'Control test pass/fail rates'**
(b) Compliance monitoring; and
**Example: 'Regulatory audit findings'**
(c) Change monitoring."
**Example: 'Configuration drift detection'**
CA-7(5)
Employ the following actions to validate that policies are established and implemented controls are operating in a consistent manner: [Assignment: organization-defined actions].
**Example: 'Automated policy compliance scans'**
CA-7(6)
Ensure the accuracy, currency, and availability of monitoring results for the system using [Assignment: organization-defined automated mechanisms].
**Example: 'Splunk + ServiceNow integration'**
CA-8
Conduct penetration testing [Assignment: organization-defined frequency] on [Assignment: organization-defined systems or system components].
**Example: 'Annual red team exercise on internet-facing systems'**
CA-8(1)
Employ an independent penetration testing agent or team to perform penetration testing on the system or system components.
**Example: 'External pentest firm with no internal access'**
CA-8(2)
Employ the following red-team exercises to simulate attempts by adversaries to compromise organizational systems in accordance with applicable rules of engagement: [Assignment: organization-defined red team exercises].
**Example: 'APT28 simulation with C2 infrastructure'**
CA-8(3)
Employ a penetration testing process that includes [Assignment: organization-defined frequency] [Selection: announced; unannounced] attempts to bypass or circumvent controls associated with physical access points to the facility.
**Example: 'Quarterly unannounced tailgating tests'**
CA-9
"a. Authorize internal connections of [Assignment: organization-defined system components or classes of components] to the system;
**Example: 'Approve dev server connecting to prod DB'**
b. Document, for each internal connection, the interface characteristics, security and privacy requirements, and the nature of the information communicated;
**Example: 'JDBC port 1433, read-only financial data'**
c. Terminate internal system connections after [Assignment: organization-defined conditions]; and
**Example: 'After project completion'**
d. Review [Assignment: organization-defined frequency] the continued need for each internal connection."
**Example: 'Quarterly connection review'**
CA-9(1)
Perform security and privacy compliance checks on constituent system components prior to the establishment of the internal connection.
**Example: 'STIG checklist before VM connection'**
CM-1
"a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] configuration management policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
**Example: 'All changes require CCB approval'**
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
2. Procedures to facilitate the implementation of the configuration management policy and the associated configuration management controls;
**Example: 'GitOps workflow for infrastructure'**
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the configuration management policy and procedures; and
**Example: 'Configuration Control Board Chair'**
c. Review and update the current configuration management:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
**Example: 'Annually and after major breaches'**
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]."
**Example: 'After tool upgrades'**
CM-2
"a. Develop, document, and maintain under configuration control, a current baseline configuration of the system; and
**Example: 'CIS Benchmark hardened image'**
b. Review and update the baseline configuration of the system:
1. [Assignment: organization-defined frequency];
**Example: 'Quarterly'**
2. When required due to [Assignment: organization-defined circumstances]; and
**Example: 'Critical vulns or new STIGs'**
3. When system components are installed or upgraded."
**Example: 'After Windows patch Tuesday'**
CM-11(1)
[Withdrawn: Incorporated into CM-8(3).]
CM-2(2)
Maintain the currency, completeness, accuracy, and availability of the baseline configuration of the system using [Assignment: organization-defined automated mechanisms].
**Example: 'Ansible Tower syncs with Git repo'**
CM-2(3)
Retain [Assignment: organization-defined number] of previous versions of baseline configurations of the system to support rollback.
**Example: 'Keep 5 previous baseline versions'**
CM-2(1)
[Withdrawn: Incorporated into CM-2.]
CM-2(4)
[Withdrawn: Incorporated into CM-7(4).]
CM-2(6)
Maintain a baseline configuration for system development and test environments that is managed separately from the operational baseline configuration.
**Example: 'Separate Git branches: dev/test vs prod'**
CM-2(7)
"(a) Issue [Assignment: organization-defined systems or system components] with [Assignment: organization-defined configurations] to individuals traveling to locations that the organization deems to be of significant risk; and
**Example: 'Air-gapped laptops for high-risk travel'**
(b) Apply the following controls to the systems or components when the individuals return from travel: [Assignment: organization-defined controls]."
**Example: 'Full scan + media wipe on return'**
CM-3
"a. Determine and document the types of changes to the system that are configuration-controlled;
**Example: 'All code deploys, firewall rules'**
b. Review proposed configuration-controlled changes to the system and approve or disapprove such changes with explicit consideration for security and privacy impact analyses;
**Example: 'CCB reviews with risk scoring'**
c. Document configuration change decisions associated with the system;
**Example: 'Jira tickets with approval signatures'**
d. Implement approved configuration-controlled changes to the system;
**Example: 'Automated deploy via Jenkins pipeline'**
e. Retain records of configuration-controlled changes to the system for [Assignment: organization-defined time period];
**Example: '7 years per records retention'**
f. Monitor and review activities associated with configuration-controlled changes to the system; and
**Example: 'Post-deploy validation scans'**
g. Coordinate and provide oversight for configuration change control activities through [Assignment: organization-defined configuration change control element] that convenes [Selection (one or more): [Assignment: organization-defined frequency]; when [Assignment: organization-defined configuration change conditions]]."
**Example: 'Weekly CCB + emergency changes'**
CM-3(1)
"Use [Assignment: organization-defined automated mechanisms] to:
(a) Document proposed changes to the system;
**Example: 'Git commit messages'**
(b) Notify [Assignment: organization-defined approval authorities] of proposed changes to the system and request change approval;
**Example: 'Slack notifications to CCB'**
(c) Highlight proposed changes to the system that have not been approved or disapproved within [Assignment: organization-defined time period];
**Example: 'Auto-escalate after 24 hours'**
(d) Prohibit changes to the system until designated approvals are received;
**Example: 'Pipeline blocks without approval'**
(e) Document all changes to the system; and
**Example: 'Immutable audit trail'**
(f) Notify [Assignment: organization-defined personnel] when approved changes to the system are completed."
**Example: 'Success notification to stakeholders'**
CM-3(2)
Test, validate, and document changes to the system before finalizing the implementation of the changes.
**Example: 'CI/CD with unit/integration/security tests'**
CM-3(3)
Implement changes to the current system baseline and deploy the updated baseline across the installed base using [Assignment: organization-defined automated mechanisms].
**Example: 'Puppet pushes baseline to 1000+ servers'**
CM-3(4)
Require [Assignment: organization-defined security and privacy representatives] to be members of the [Assignment: organization-defined configuration change control element].
**Example: 'ISSM mandatory CCB member'**
CM-3(5)
Implement the following security responses automatically if baseline configurations are changed in an unauthorized manner: [Assignment: organization-defined security responses].
**Example: 'Auto-quarantine + alert on drift detection'**
CM-3(6)
Ensure that cryptographic mechanisms used to provide the following controls are under configuration management: [Assignment: organization-defined controls].
**Example: 'TLS certs in HashiCorp Vault'**
CM-3(7)
Review changes to the system [Assignment: organization-defined frequency] or when [Assignment: organization-defined circumstances] to determine whether unauthorized changes have occurred.
**Example: 'Daily config drift reports'**
CM-3(8)
Prevent or restrict changes to the configuration of the system under the following circumstances: [Assignment: organization-defined circumstances].
**Example: 'Read-only mode during ATO assessment'**
CM-4
Analyze changes to the system to determine potential security and privacy impacts prior to change implementation.
**Example: 'SCA + threat model review in pipeline'**
CM-4(1)
Analyze changes to the system in a separate test environment before implementation in an operational environment, looking for security and privacy impacts due to flaws, weaknesses, incompatibility, or intentional malice.
**Example: 'Staging environment mirror of prod'**
CM-4(2)
After system changes, verify that the impacted controls are implemented correctly, operating as intended, and producing the desired outcome with regard to meeting the security and privacy requirements for the system.
**Example: 'Post-deploy control validation suite'**
CM-5
Define, document, approve, and enforce physical and logical access restrictions associated with changes to the system.
**Example: 'Change windows only from approved jump hosts'**
CM-5(1)
"(a) Enforce access restrictions using [Assignment: organization-defined automated mechanisms]; and
**Example: 'PAM + bastion host access'**
(b) Automatically generate audit records of the enforcement actions."
**Example: 'Log all sudo commands'**
CM-2(5)
[Withdrawn: Incorporated into CM-7(5).]
CM-5(2)
[Withdrawn: Incorporated into CM-3(7).]
CM-5(4)
Enforce dual authorization for implementing changes to [Assignment: organization-defined system components and system-level information].
**Example: 'Two-person rule for prod DB schema changes'**
CM-5(5)
"(a) Limit privileges to change system components and system-related information within a production or operational environment; and
**Example: 'Read-only prod for developers'**
(b) Review and reevaluate privileges [Assignment: organization-defined frequency]."
**Example: 'Monthly privileged access review'**
CM-5(6)
Limit privileges to change software resident within software libraries.
**Example: 'Protected RPM/YUM repositories'**
CM-5(3)
[Withdrawn: Moved to CM-14.]
CM-6
"a. Establish and document configuration settings for components employed within the system that reflect the most restrictive mode consistent with operational requirements using [Assignment: organization-defined common secure configurations];
**Example: 'CIS Benchmarks for Windows/Linux'**
b. Implement the configuration settings;
**Example: 'Chef enforces STIG compliance'**
c. Identify, document, and approve any deviations from established configuration settings for [Assignment: organization-defined system components] based on [Assignment: organization-defined operational requirements]; and
**Example: 'Documented exception for legacy app port'**
d. Monitor and control changes to the configuration settings in accordance with organizational policies and procedures."
**Example: 'Weekly SCAP compliance scans'**
CM-6(1)
Manage, apply, and verify configuration settings for [Assignment: organization-defined system components] using [Assignment: organization-defined automated mechanisms].
**Example: 'SCCM + OpenSCAP automated enforcement'**
CM-6(2)
Take the following actions in response to unauthorized changes to [Assignment: organization-defined configuration settings]: [Assignment: organization-defined actions].
**Example: 'Auto-revert + alert within 5 minutes'**
CM-5(7)
[Withdrawn: Incorporated into SI-7.]
CM-6(3)
[Withdrawn: Incorporated into SI-7.]
CM-7
"a. Configure the system to provide only [Assignment: organization-defined mission essential capabilities]; and
**Example: 'Disable telnet, enable only SSH'**
b. Prohibit or restrict the use of the following functions, ports, protocols, software, and/or services: [Assignment: organization-defined prohibited or restricted functions, system ports, protocols, software, and/or services]."
**Example: 'Block SMBv1, RDP port 3389'**
CM-7(1)
"(a) Review the system [Assignment: organization-defined frequency] to identify unnecessary and/or nonsecure functions, ports, protocols, software, and services; and
**Example: 'Monthly Nessus scan for open ports'**
(b) Disable or remove [Assignment: organization-defined functions, ports, protocols, software, and services within the system deemed to be unnecessary and/or nonsecure]."
**Example: 'Auto-disable unused Windows features'**
CM-7(2)
Prevent program execution in accordance with [Selection (one or more): [Assignment: organization-defined policies, rules of behavior, and/or access agreements regarding software program usage and restrictions]; rules authorizing the terms and conditions of software program usage].
**Example: 'AppLocker whitelisting policy'**
CM-7(3)
Ensure compliance with [Assignment: organization-defined registration requirements for functions, ports, protocols, and services].
**Example: 'All ports documented in CM-8 inventory'**
CM-7(4)
"(a) Identify [Assignment: organization-defined software programs not authorized to execute on the system];
**Example: 'Block torrent clients, games'**
(b) Employ an allow-all, deny-by-exception policy to prohibit the execution of unauthorized software programs on the system; and
**Example: 'Blocklist via Windows Defender'**
(c) Review and update the list of unauthorized software programs [Assignment: organization-defined frequency]."
**Example: 'Monthly blocklist review'**
CM-7(5)
"(a) Identify [Assignment: organization-defined software programs authorized to execute on the system];
**Example: 'Only approved 200 business apps'**
(b) Employ a deny-all, permit-by-exception policy to allow the execution of authorized software programs on the system; and
**Example: 'Tanium application control'**
(c) Review and update the list of authorized software programs [Assignment: organization-defined frequency]."
**Example: 'Quarterly application review'**
CM-7(6)
Require that the following user-installed software execute in a confined physical or virtual machine environment with limited privileges: [Assignment: organization-defined user-installed software].
**Example: 'Browser extensions in sandbox'**
CM-7(7)
"Allow execution of binary or machine-executable code only in confined physical or virtual machine environments and with the explicit approval of [Assignment: organization-defined personnel or roles] when such code is:
(a) Obtained from sources with limited or no warranty; and/or
**Example: 'Unsigned 3rd party utilities'**
(b) Without the provision of source code."
**Example: 'Compiled research tools'**
CM-7(8)
"(a) Prohibit the use of binary or machine-executable code from sources with limited or no warranty or without the provision of source code; and
**Example: 'No unsigned executables allowed'**
(b) Allow exceptions only for compelling mission or operational requirements and with the approval of the authorizing official."
**Example: 'AO approves legacy forensics tool'**
CM-7(9)
"(a) Identify [Assignment: organization-defined hardware components authorized for system use];
**Example: 'Dell servers, Cisco switches only'**
(b) Prohibit the use or connection of unauthorized hardware components;
**Example: 'NAC blocks unknown MAC addresses'**
(c) Review and update the list of authorized hardware components [Assignment: organization-defined frequency]."
**Example: 'Annual hardware inventory review'**
CM-8
"a. Develop and document an inventory of system components that:
1. Accurately reflects the system;
2. Includes all components within the system;
**Example: 'Servers, VMs, containers, IoT devices'**
3. Does not include duplicate accounting of components or components assigned to any other system;
4. Is at the level of granularity deemed necessary for tracking and reporting; and
**Example: 'UUID + hostname + IP + MAC'**
5. Includes the following information to achieve system component accountability: [Assignment: organization-defined information deemed necessary to achieve effective system component accountability]; and
**Example: 'Asset tag, owner, location, patch level'**
b. Review and update the system component inventory [Assignment: organization-defined frequency]."
**Example: 'Daily automated discovery scan'**
CM-8(1)
Update the inventory of system components as part of component installations, removals, and system updates.
**Example: 'Auto-update CMDB on VM provisioning'**
CM-8(2)
Maintain the currency, completeness, accuracy, and availability of the inventory of system components using [Assignment: organization-defined automated mechanisms].
**Example: 'ServiceNow CMDB with API sync'**
CM-8(3)
"(a) Detect the presence of unauthorized hardware, software, and firmware components within the system using [Assignment: organization-defined automated mechanisms] [Assignment: organization-defined frequency]; and
**Example: 'Tanium integrity monitoring hourly'**
(b) Take the following actions when unauthorized components are detected: [Selection (one or more): disable network access by such components; isolate the components; notify [Assignment: organization-defined personnel or roles]]."
**Example: 'Quarantine + page SOC team'**
CM-8(4)
Include in the system component inventory information, a means for identifying by [Selection (one or more): name; position; role], individuals responsible and accountable for administering those components.
**Example: 'Server123 → Admin: jdoe@company.com'**
CM-6(4)
[Withdrawn: Incorporated into CM-4.]
CM-8(6)
Include assessed component configurations and any approved deviations to current deployed configurations in the system component inventory.
**Example: 'Server456: CIS Level 1 with 2 exceptions'**
CM-8(7)
Provide a centralized repository for the inventory of system components.
**Example: 'Single pane of glass CMDB dashboard'**
CM-8(8)
Support the tracking of system components by geographic location using [Assignment: organization-defined automated mechanisms].
**Example: 'DHCP location + CMDB geo-tagging'**
CM-8(9)
"(a) Assign system components to a system; and
**Example: 'VM123 assigned to Payroll system'**
(b) Receive an acknowledgment from [Assignment: organization-defined personnel or roles] of this assignment."
**Example: 'System owner email confirmation'**
CM-9
"Develop, document, and implement a configuration management plan for the system that:
a. Addresses roles, responsibilities, and configuration management processes and procedures;
**Example: 'DevOps team owns IaC pipeline'**
b. Establishes a process for identifying configuration items throughout the system development life cycle and for managing the configuration of the configuration items;
**Example: 'Git tags for every release'**
c. Defines the configuration items for the system and places the configuration items under configuration management;
**Example: 'Code, docs, configs as CIs'**
d. Is reviewed and approved by [Assignment: organization-defined personnel or roles]; and
**Example: 'AO approves CMP'**
e. Protects the configuration management plan from unauthorized disclosure and modification."
**Example: 'Encrypted Git repo with RBAC'**
CM-9(1)
Assign responsibility for developing the configuration management process to organizational personnel that are not directly involved in system development.
**Example: 'QA team owns CM process'**
CM-10
"a. Use software and associated documentation in accordance with contract agreements and copyright laws;
**Example: 'Microsoft volume licensing compliance'**
b. Track the use of software and associated documentation protected by quantity licenses to control copying and distribution; and
**Example: 'Flexera license manager'**
c. Control and document the use of peer-to-peer file sharing technology to ensure that this capability is not used for the unauthorized distribution, display, performance, or reproduction of copyrighted work."
**Example: 'Block BitTorrent on corporate network'**
CM-10(1)
Establish the following restrictions on the use of open-source software: [Assignment: organization-defined restrictions].
**Example: 'No GPL code in proprietary products'**
CM-11
"a. Establish [Assignment: organization-defined policies] governing the installation of software by users;
**Example: 'No unauthorized software installs'**
b. Enforce software installation policies through the following methods: [Assignment: organization-defined methods]; and
**Example: 'Group Policy + endpoint protection'**
c. Monitor policy compliance [Assignment: organization-defined frequency]."
**Example: 'Weekly endpoint compliance reports'**
CM-8(5)
[Withdrawn: Incorporated into CM-8.]
CM-11(2)
Allow user installation of software only with explicit privileged status.
**Example: 'Admin rights required for installs'**
CM-11(3)
Enforce and monitor compliance with software installation policies using [Assignment: organization-defined automated mechanisms].
**Example: 'Carbon Black unauthorized install alerts'**
CM-12
"a. Identify and document the location of [Assignment: organization-defined information] and the specific system components on which the information is processed and stored;
**Example: 'Customer PII → DB server DC01'**
b. Identify and document the users who have access to the system and system components where the information is processed and stored; and
**Example: 'Finance team + auditors'**
c. Document changes to the location (i.e., system or system components) where the information is processed and stored."
**Example: 'Migration from on-prem to AWS S3'**
CM-12(1)
Use automated tools to identify [Assignment: organization-defined information by information type] on [Assignment: organization-defined system components] to ensure controls are in place to protect organizational information and individual privacy.
**Example: 'Nightfall DLP scans for PII patterns'**
CM-13
Develop and document a map of system data actions.
**Example: 'Data flow diagram: ingest → process → store → archive'**
CM-14
Prevent the installation of [Assignment: organization-defined software and firmware components] without verification that the component has been digitally signed using a certificate that is recognized and approved by the organization.
**Example: 'Windows SmartScreen + trusted CA list'**
Here is the NIST 800-53 MA-SR document with brief example descriptions inserted for each control requirement:
```html
MA-2(1)
[Withdrawn: Incorporated into MA-2.]
MA-2(2)
"(a) Schedule, conduct, and document maintenance, repair, and replacement actions for the system using [Assignment: organization-defined automated mechanisms]; and
**Example: 'ServiceNow CMDB tracks all maintenance tickets'**
(b) Produce up-to date, accurate, and complete records of all maintenance, repair, and replacement actions requested, scheduled, in process, and completed."
**Example: 'Real-time dashboard shows maintenance status'**
MA-3
"a. Approve, control, and monitor the use of system maintenance tools; and
**Example: 'Approved tools: PuTTY, WinSCP, Wireshark'**
b. Review previously approved system maintenance tools [Assignment: organization-defined frequency]."
**Example: 'Quarterly tool inventory review'**
MA-3(1)
Inspect the maintenance tools used by maintenance personnel for improper or unauthorized modifications.
**Example: 'Hash verification of vendor diagnostic tools'**
MA-3(2)
Check media containing diagnostic and test programs for malicious code before the media are used in the system.
**Example: 'VirusTotal scan USB boot media'**
MA-3(3)
"Prevent the removal of maintenance equipment containing organizational information by:
(a) Verifying that there is no organizational information contained on the equipment;
**Example: 'DBAN wipe verification'**
(b) Sanitizing or destroying the equipment;
**Example: 'NSA-approved shredder for HDDs'**
(c) Retaining the equipment within the facility; or
**Example: 'Vendor onsite maintenance only'**
(d) Obtaining an exemption from [Assignment: organization-defined personnel or roles] explicitly authorizing removal of the equipment from the facility."
**Example: 'AO approves escorted removal'**
MA-3(4)
Restrict the use of maintenance tools to authorized personnel only.
**Example: 'Tool access via CyberArk PAM'**
MA-3(5)
Monitor the use of maintenance tools that execute with increased privilege.
**Example: 'Audit all root-level diagnostic runs'**
MA-3(6)
Inspect maintenance tools to ensure the latest software updates and patches are installed.
**Example: 'Weekly WSUS scan of vendor tool laptops'**
MA-4
"a. Approve and monitor nonlocal maintenance and diagnostic activities;
**Example: 'Pre-approved vendor remote access windows'**
b. Allow the use of nonlocal maintenance and diagnostic tools only as consistent with organizational policy and documented in the security plan for the system;
**Example: 'Only approved TeamViewer version'**
c. Employ strong authentication in the establishment of nonlocal maintenance and diagnostic sessions;
**Example: 'MFA + TOA for remote access'**
d. Maintain records for nonlocal maintenance and diagnostic activities; and
**Example: 'Session recordings + access logs'**
e. Terminate session and network connections when nonlocal maintenance is completed."
**Example: 'Auto-disconnect after 30 minutes idle'**
MA-4(1)
"(a) Log [Assignment: organization-defined audit events] for nonlocal maintenance and diagnostic sessions; and
**Example: 'All commands, file transfers, duration'**
(b) Review the audit records of the maintenance and diagnostic sessions to detect anomalous behavior."
**Example: 'Daily SOC review of vendor sessions'**
MA-4(2)
[Withdrawn: Incorporated into MA-1 and MA-4.]
MA-4(3)
"(a) Require that nonlocal maintenance and diagnostic services be performed from a system that implements a security capability comparable to the capability implemented on the system being serviced; or
**Example: 'Vendor laptop meets STIG requirements'**
(b) Remove the component to be serviced from the system prior to nonlocal maintenance or diagnostic services; sanitize the component (for organizational information); and after the service is performed, inspect and sanitize the component (for potentially malicious software) before reconnecting the component to the system."
**Example: 'HDD removed, wiped, rescanned before reinstall'**
MA-4(4)
"Protect nonlocal maintenance sessions by:
(a) Employing [Assignment: organization-defined authenticators that are replay resistant]; and
**Example: 'Kerberos tickets + TOA'**
(b) Separating the maintenance sessions from other network sessions with the system by either:
(1) Physically separated communications paths; or
**Example: 'Dedicated maintenance VLAN'**
(2) Logically separated communications paths."
**Example: 'IPsec tunnel with separate firewall rules'**
MA-4(5)
"(a) Require the approval of each nonlocal maintenance session by [Assignment: organization-defined personnel or roles]; and
**Example: 'ISSM approves each session'**
(b) Notify the following personnel or roles of the date and time of planned nonlocal maintenance: [Assignment: organization-defined personnel or roles]."
**Example: '24-hour advance notice to SOC'**
MA-4(6)
Implement the following cryptographic mechanisms to protect the integrity and confidentiality of nonlocal maintenance and diagnostic communications: [Assignment: organization-defined cryptographic mechanisms].
**Example: 'TLS 1.3 + SHA-256 for all remote sessions'**
MA-4(7)
Verify session and network connection termination after the completion of nonlocal maintenance and diagnostic sessions.
**Example: 'Automated post-session connectivity scan'**
MA-5
"a. Establish a process for maintenance personnel authorization and maintain a list of authorized maintenance organizations or personnel;
**Example: 'Approved vendors: Dell, Cisco, Microsoft'**
b. Verify that non-escorted personnel performing maintenance on the system possess the required access authorizations; and
**Example: 'Check badges + clearance before entry'**
c. Designate organizational personnel with required access authorizations and technical competence to supervise the maintenance activities of personnel who do not possess the required access authorizations."
**Example: 'Cleared engineer escorts vendor tech'**
MA-5(1)
"(a) Implement procedures for the use of maintenance personnel that lack appropriate security clearances or are not U.S. citizens, that include the following requirements:
(1) Maintenance personnel who do not have needed access authorizations, clearances, or formal access approvals are escorted and supervised during the performance of maintenance and diagnostic activities on the system by approved organizational personnel who are fully cleared, have appropriate access authorizations, and are technically qualified; and
**Example: 'US person escorts foreign vendor'**
(2) Prior to initiating maintenance or diagnostic activities by personnel who do not have needed access authorizations, clearances or formal access approvals, all volatile information storage components within the system are sanitized and all nonvolatile storage media are removed or physically disconnected from the system and secured; and
**Example: 'RAM cleared, HDD removed before vendor work'**
(b) Develop and implement [Assignment: organization-defined alternate controls] in the event a system component cannot be sanitized, removed, or disconnected from the system."
**Example: 'Two-person integrity observed'**
MA-5(2)
Verify that personnel performing maintenance and diagnostic activities on a system processing, storing, or transmitting classified information possess security clearances and formal access approvals for at least the highest classification level and for compartments of information on the system.
**Example: 'TS/SCI with SIPRNET access for SCIF work'**
MA-5(3)
Verify that personnel performing maintenance and diagnostic activities on a system processing, storing, or transmitting classified information are U.S. citizens.
**Example: 'E-Verify check for all cleared personnel'**
MA-5(4)
"Ensure that:
(a) Foreign nationals with appropriate security clearances are used to conduct maintenance and diagnostic activities on classified systems only when the systems are jointly owned and operated by the United States and foreign allied governments, or owned and operated solely by foreign allied governments; and
**Example: 'NATO ally maintenance on shared radar'**
(b) Approvals, consents, and detailed operational conditions regarding the use of foreign nationals to conduct maintenance and diagnostic activities on classified systems are fully documented within Memoranda of Agreements."
**Example: 'SOFA agreement specifies maintenance roles'**
MA-5(5)
Ensure that non-escorted personnel performing maintenance activities not directly associated with the system but in the physical proximity of the system, have required access authorizations.
**Example: 'HVAC tech in SCIF needs Secret clearance'**
MA-6
Obtain maintenance support and/or spare parts for [Assignment: organization-defined system components] within [Assignment: organization-defined time period] of failure.
**Example: '4-hour SLA for critical server parts'**
MA-6(1)
Perform preventive maintenance on [Assignment: organization-defined system components] at [Assignment: organization-defined time intervals].
**Example: 'Quarterly UPS battery replacement'**
MA-6(2)
Perform predictive maintenance on [Assignment: organization-defined system components] at [Assignment: organization-defined time intervals].
**Example: 'AI-driven HDD failure prediction'**
MA-6(3)
Transfer predictive maintenance data to a maintenance management system using [Assignment: organization-defined automated mechanisms].
**Example: 'IoT sensors → ServiceNow CMDB'**
MA-7
Restrict or prohibit field maintenance on [Assignment: organization-defined systems or system components] to [Assignment: organization-defined trusted maintenance facilities].
**Example: 'Crypto equipment serviced only at NSA facility'**
MP-1
"a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] media protection policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
**Example: 'All removable media encrypted with BitLocker'**
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
2. Procedures to facilitate the implementation of the media protection policy and the associated media protection controls;
**Example: 'Media sanitization SOP'**
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the media protection policy and procedures; and
**Example: 'Media Protection Officer'**
c. Review and update the current media protection:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
**Example: 'Annually and after data breach'**
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]."
**Example: 'After new NIST 800-88 revision'**
MP-2
Restrict access to [Assignment: organization-defined types of digital and/or non-digital media] to [Assignment: organization-defined personnel or roles].
**Example: 'USB drives only for IT security team'**
MP-2(1)
[Withdrawn: Incorporated into MP-4(2).]
MP-2(2)
[Withdrawn: Incorporated into SC-28(1).]
MP-3
"a. Mark system media indicating the distribution limitations, handling caveats, and applicable security markings (if any); and
**Example: 'UNCLASS//FOUO label on USB drives'**
b. Exempt [Assignment: organization-defined types of system media] from marking if the media remain within [Assignment: organization-defined controlled areas]."
**Example: 'No labels needed in locked server room'**
MP-4
"a. Physically control and securely store [Assignment: organization-defined types of digital and/or non-digital media] within [Assignment: organization-defined controlled areas]; and
**Example: 'Locked media safes in SCIF'**
b. Protect system media types defined in MP-4a until the media are destroyed or sanitized using approved equipment, techniques, and procedures."
**Example: 'Iron Mountain certified destruction'**
MP-4(1)
[Withdrawn: Incorporated into SC-28(1).]
MP-4(2)
Restrict access to media storage areas and log access attempts and access granted using [Assignment: organization-defined automated mechanisms].
**Example: 'HID badge reader + audit trail'**
MP-5
"a. Protect and control [Assignment: organization-defined types of system media] during transport outside of controlled areas using [Assignment: organization-defined controls];
**Example: 'Tamper-evident bags + chain of custody'**
b. Maintain accountability for system media during transport outside of controlled areas;
**Example: 'Signed handoff forms'**
c. Document activities associated with the transport of system media; and
**Example: 'FedEx tracking + custody logs'**
d. Restrict the activities associated with the transport of system media to authorized personnel."
**Example: 'Courier with Secret clearance only'**
MP-5(1)
[Withdrawn: Incorporated into MP-5.]
MP-5(2)
[Withdrawn: Incorporated into MP-5.]
MP-5(3)
Employ an identified custodian during transport of system media outside of controlled areas.
**Example: 'Designated courier with two escorts'**
MP-5(4)
[Withdrawn: Incorporated into SC-28(1).]
MP-6
"a. Sanitize [Assignment: organization-defined system media] prior to disposal, release out of organizational control, or release for reuse using [Assignment: organization-defined sanitization techniques and procedures]; and
**Example: 'DoD 5220.22-M 3-pass wipe'**
b. Employ sanitization mechanisms with the strength and integrity commensurate with the security category or classification of the information."
**Example: 'Clearable vs Secret media requirements'**
MP-6(1)
Review, approve, track, document, and verify media sanitization and disposal actions.
**Example: 'Sanitization certificate of destruction'**
MP-6(2)
Test sanitization equipment and procedures [Assignment: organization-defined frequency] to ensure that the intended sanitization is being achieved.
**Example: 'Monthly DBAN test on known data'**
MP-6(3)
Apply nondestructive sanitization techniques to portable storage devices prior to connecting such devices to the system under the following circumstances: [Assignment: organization-defined circumstances requiring sanitization of portable storage devices].
**Example: 'All found USB drives wiped before use'**
MP-6(4)
[Withdrawn: Incorporated into MP-6.]
MP-6(5)
[Withdrawn: Incorporated into MP-6.]
MP-6(6)
[Withdrawn: Incorporated into MP-6.]
MP-6(7)
Enforce dual authorization for the sanitization of [Assignment: organization-defined system media].
**Example: 'Two-person rule for Secret media destruction'**
MP-6(8)
Provide the capability to purge or wipe information from [Assignment: organization-defined systems or system components] [Selection: remotely; under the following conditions: [Assignment: organization-defined conditions]].
**Example: 'Intune remote wipe for lost laptops'**
MP-7
"a. [Selection: Restrict; Prohibit] the use of [Assignment: organization-defined types of system media] on [Assignment: organization-defined systems or system components] using [Assignment: organization-defined controls]; and
**Example: 'No personal USB drives allowed'**
b. Prohibit the use of portable storage devices in organizational systems when such devices have no identifiable owner."
**Example: 'Block unknown USB serial numbers'**
MP-7(1)
[Withdrawn: Incorporated into MP-7.]
MP-7(2)
Prohibit the use of sanitization-resistant media in organizational systems.
**Example: 'No M-DISC or archival gold CDs'**
MP-8
"a. Establish [Assignment: organization-defined system media downgrading process] that includes employing downgrading mechanisms with strength and integrity commensurate with the security category or classification of the information;
**Example: 'NIAPC-approved downgrader'**
b. Verify that the system media downgrading process is commensurate with the security category and/or classification level of the information to be removed and the access authorizations of the potential recipients of the downgraded information;
**Example: 'Secret → Unclass with human review'**
c. Identify [Assignment: organization-defined system media requiring downgrading]; and
**Example: 'Files for public release'**
d. Downgrade the identified system media using the established process."
**Example: 'Automated DLP + manual inspection'**
MP-8(1)
Document system media downgrading actions.
**Example: 'Downgrade certificate signed by two officers'**
MP-8(2)
Test downgrading equipment and procedures [Assignment: organization-defined frequency] to ensure that downgrading actions are being achieved.
**Example: 'Quarterly test with known classified data'**
MP-8(3)
Downgrade system media containing controlled unclassified information prior to public release.
**Example: 'Redact CUI before FOIA response'**
MP-8(4)
Downgrade system media containing classified information prior to release to individuals without required access authorizations.
**Example: 'Declassify before contractor access'**
PE-1
"a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] physical and environmental protection policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
**Example: '24/7 guarded facility access'**
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
2. Procedures to facilitate the implementation of the physical and environmental protection policy and the associated physical and environmental protection controls;
**Example: 'SCIF SOPs and visitor logs'**
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the physical and environmental protection policy and procedures; and
**Example: 'Physical Security Manager'**
c. Review and update the current physical and environmental protection:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
**Example: 'Annually and after facility changes'**
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]."
**Example: 'After fire drill lessons learned'**
PE-2
"a. Develop, approve, and maintain a list of individuals with authorized access to the facility where the system resides;
**Example: 'Active Directory group: Facility_Access'**
b. Issue authorization credentials for facility access;
**Example: 'HID proximity cards with photo'**
c. Review the access list detailing authorized facility access by individuals [Assignment: organization-defined frequency]; and
**Example: 'Quarterly access roster review'**
d. Remove individuals from the facility access list when access is no longer required."
**Example: 'Auto-revoke on HR termination'**
PE-2(1)
Authorize physical access to the facility where the system resides based on position or role.
**Example: 'DBA role = server room access'**
PE-2(2)
Require two forms of identification from the following forms of identification for visitor access to the facility where the system resides: [Assignment: organization-defined list of acceptable forms of identification].
**Example: 'Govt ID + company badge'**
PE-2(3)
Restrict unescorted access to the facility where the system resides to personnel with [Selection (one or more): security clearances for all information contained within the system; formal access authorizations for all information contained within the system; need for access to all information contained within the system; [Assignment: organization-defined physical access authorizations]].
**Example: 'Secret clearance for SCIF unescorted access'**
PE-3
"a. Enforce physical access authorizations at [Assignment: organization-defined entry and exit points to the facility where the system resides] by:
1. Verifying individual access authorizations before granting access to the facility; and
**Example: 'Biometric + PIN at SCIF door'**
2. Controlling ingress and egress to the facility using [Selection (one or more): [Assignment: organization-defined physical access control systems or devices]; guards];
**Example: 'Turnstiles + armed guards'**
b. Maintain physical access audit logs for [Assignment: organization-defined entry or exit points];
**Example: 'Lenel OnGuard 90-day retention'**
c. Control access to areas within the facility designated as publicly accessible by implementing the following controls: [Assignment: organization-defined physical access controls];
**Example: 'Lobby badge required beyond reception'**
d. Escort visitors and control visitor activity [Assignment: organization-defined circumstances requiring visitor escorts and control of visitor activity];
**Example: 'All visitors escorted in SCIF'**
e. Secure keys, combinations, and other physical access devices;
**Example: 'Keys in GSA-approved safe'**
f. Inventory [Assignment: organization-defined physical access devices] every [Assignment: organization-defined frequency]; and
**Example: 'Monthly badge inventory'**
g. Change combinations and keys [Assignment: organization-defined frequency] and/or when keys are lost, combinations are compromised, or when individuals possessing the keys or combinations are transferred or terminated."
**Example: 'Quarterly combo changes'**
PE-3(1)
Enforce physical access authorizations to the system in addition to the physical access controls for the facility at [Assignment: organization-defined physical spaces containing one or more components of the system].
**Example: 'Separate cage locks for prod servers'**
PE-3(2)
Perform security checks [Assignment: organization-defined frequency] on individuals entering areas within the facility containing systems or system components.
**Example: 'Random bag searches at server room'**
PE-3(3)
Control access to areas within controlled facility areas containing system wiring by implementing the following controls: [Assignment: organization-defined physical access controls].
**Example: 'Conduit locks + tamper seals'**
PE-6
Monitor physical access to the facility where the system resides to detect and respond to physical security incidents.
**Example: '24/7 CCTV with motion detection'**
PE-6(1)
Deactivate authentication credentials when individuals are no longer employed or no longer require authorized access to the facility.
**Example: 'Immediate badge deactivation on termination'**
PE-6(2)
Enforce physical access authorizations to areas within controlled facility areas containing systems or system components by verifying individual access authorizations before granting access.
**Example: 'Mantrap with two-factor at data center'**
PE-6(3)
Control physical access to areas within controlled facility areas containing systems or system components using the following controls: [Assignment: organization-defined physical access controls].
**Example: 'Biometric locks on server racks'**
PE-8
Provide a fire suppression capability for the facility where the system resides that is appropriate for the information processed, stored, and transmitted by the system.
**Example: 'Clean agent FM-200 system'**
PE-9
Protect power equipment and power cabling for the system from damage.
**Example: 'UPS with seismic bracing'**
PE-10
Implement controls to maintain the following temperature and humidity levels within the facility where the system resides: [Assignment: organization-defined temperature and humidity levels].
**Example: '64-74°F, 40-60% RH per ASHRAE'**
PE-11
Implement controls to limit electromagnetic emanations from the system.
**Example: 'TEMPEST-certified equipment in SCIF'**
PE-12
Implement controls to prevent unauthorized disclosure of information based on lighting within the facility where the system resides.
**Example: 'Motion-activated lights in server room'**
PE-13
Implement controls to protect against unauthorized physical access to the system while in transit.
**Example: 'Armored courier for server shipment'**
PE-13(1)
Employ [Assignment: organization-defined controls] to protect against unauthorized physical access while the system or system component is in transit.
**Example: 'GPS tracking + tamper-evident seals'**
PE-13(2)
Employ the following controls to protect the system or system component during transport: [Assignment: organization-defined controls].
**Example: 'Foam packing + climate-controlled truck'**
PE-13(3)
Maintain continuous custody of system or system components during transport.
**Example: 'Two-person handoff chain'**
PE-14
"(a) Provide emergency power sources;
**Example: '48-hour diesel generator'**
(b) Provide appropriate fault tolerance for system power equipment;
**Example: 'N+1 UPS configuration'**
(c) Implement controls to protect against unauthorized physical access to power equipment;
**Example: 'Locked electrical rooms'**
(d) Protect power cabling from damage;
**Example: 'Conduit + rodent protection'**
(e) Implement controls to protect against unauthorized physical access to power distribution components; and
**Example: 'Biometric access to PDU'**
(f) Implement controls to protect against unauthorized physical access to emergency shutdown capability."
**Example: 'Break-glass E-stop in secure cabinet'**
PE-15
Implement controls to protect water utilities serving the facility where the system resides.
**Example: 'Backflow preventers + water alarms'**
PE-16
Implement controls to protect gas utilities serving the facility where the system resides.
**Example: 'Automatic gas shutoff valves'**
PE-18
Protect the system from unauthorized disclosure of information due to lighting within the facility where the system resides.
**Example: 'Privacy screens on all workstations'**
PE-19
Implement controls to protect the system from unauthorized physical access during and after construction of the facility where the system resides.
**Example: 'Construction surveillance program'**
PE-20
Provide visitors with a means to report unauthorized physical access attempts to the facility where the system resides.
**Example: 'Emergency call button in lobby'**
PL-1
[a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] planning policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
2. Procedures to facilitate the implementation of the planning policy and the associated planning controls;
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the planning policy and procedures; and
c. Review and update the current planning:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events].]
**Example: 'Annual SSP update process'**
PL-2
Develop a system security and privacy plan that:
a. Provides an overview of the security and privacy requirements for the system and describes the controls in place or planned for meeting those requirements, including a rationale for any tailoring decisions;
**Example: 'Tailored controls justified in SSP'**
b. Includes key information needed to implement the controls;
**Example: 'Configuration settings, ports/protocols'**
c. Describes any known weaknesses in the implemented controls;
**Example: 'Inherited control gaps identified'**
d. Includes a listing of system security and privacy roles and responsibilities;
**Example: 'RACI matrix for all roles'**
e. Is reviewed and approved by the authorizing official or designated representative prior to plan implementation;
**Example: 'AO signs SSP before ATO'**
f. Describes the process for determining whether a change to the system affects the security or privacy posture of the system;
**Example: 'Change control impact assessment'**
g. Documents planned changes to the system and the potential impact of those changes on the security and privacy posture of the system;
**Example: '30-day change forecast'**
h. Is reviewed and updated [Assignment: organization-defined frequency] and when significant changes to the system occur;
**Example: 'Annual SSP review + major changes'**
i. Reflects the authorization status of the system; and
**Example: 'ATO status and expiration date'**
j. Reflects the current implementation status of the controls.
**Example: 'Implemented/partial/planned status'**
PL-2(1)
Develop a transition plan for continuing operation of the system when the system authorization is expiring or will expire.
**Example: '60-day reauthorization plan'**
PL-2(3)
Include in the security and privacy plan, as part of the tailoring decisions, a justification for tailoring decisions that eliminates controls or control enhancements.
**Example: 'Low impact system removes high-impact controls'**
PL-2(4)
Include in the security and privacy plan, the criteria for de-selecting controls or control enhancements from the high baselines.
**Example: 'Risk-based control selection matrix'**
PL-4
Develop rules of behavior for authorized system users that:
a. Describe the rules of behavior for authorized users;
**Example: 'Acceptable use policy'**
b. Are consistent with laws, executive orders, directives, regulations, policies, standards, and guidelines;
**Example: 'FISMA-compliant AUP'**
c. Explicitly state the consequences of noncompliance; and
**Example: 'Termination for policy violations'**
d. Are acknowledged and agreed to, in writing or electronically, by authorized system users prior to authorizing access to the system.
**Example: 'Annual electronic AUP signature'**
PL-4(1)
Require authorized users to review and acknowledge the rules of behavior [Assignment: organization-defined frequency].
**Example: 'Annual AUP recertification'**
PL-8
Develop and document a contingency plan for the system that:
a. Identifies essential mission and business functions and associated contingency requirements;
**Example: 'Critical payroll processing'**
b. Provides recovery objectives, restoration priorities, and metrics;
**Example: 'RTO 4hrs, RPO 15min'**
c. Addresses contingency roles, responsibilities, assigned individuals with contact information;
**Example: 'Incident response team roster'**
d. Configures recovery strategies;
**Example: 'Hot site failover'**
e. Provides guidance on conducting backup operations;
**Example: 'Daily incremental backups'**
f. Provides guidance on conducting recovery operations;
**Example: 'Failover checklist'**
g. Requires testing, training, and exercises; and
**Example: 'Quarterly tabletop exercises'**
h. Is reviewed and approved by [Assignment: organization-defined personnel or roles].
**Example: 'AO approves COOP plan'**
PM-1
[a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] program management policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
2. Procedures to facilitate the implementation of the program management policy and the associated program management controls;
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the program management policy and procedures; and
c. Review and update the current program management:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events].]
**Example: 'Enterprise-wide cybersecurity program policy'**
PM-5
Develop an organization-wide information security and privacy program plan that provides an organization-wide approach to managing information security and privacy.
**Example: '5-year cybersecurity roadmap'**
PM-9
Develop and document an organization-wide risk management strategy that includes risk tolerance, approach, directives, policies, responsibilities, acceptable risk levels, and continuous monitoring.
**Example: 'Risk appetite statement approved by board'**
PM-12
Develop and institute an organization-wide insider threat program.
**Example: 'UEBA + HR anomaly detection'**
PM-15
Develop and document a privacy program plan that provides an organization-wide approach to managing privacy.
**Example: 'GDPR compliance roadmap'**
PM-16
Provide an organization-wide enterprise architecture that:
a. Is consistent with strategic goals and objectives;
**Example: 'Zero trust architecture roadmap'**
b. Reflects all known system security and privacy requirements;
**Example: 'Security requirements traceability matrix'**
c. Identifies all systems, system components, information flows, and dependencies; and
**Example: 'TOGAF enterprise data flow diagram'**
d. Is reviewed and updated [Assignment: organization-defined frequency].
**Example: 'Annual architecture review'**
PM-17
Develop and document supply chain risk management strategy.
**Example: 'Vendor risk assessment framework'**
PM-21
Develop and document a strategic assessment, selection, and authorization process for systems.
**Example: 'Enterprise ATO process'**
PM-24
Develop and document a continuous monitoring strategy.
**Example: 'ConMon dashboard with key metrics'**
PM-30
Develop and document a supply chain risk management plan that provides an organization-wide approach to managing supply chain risk.
**Example: 'Third-party risk management program'**
PM-31
Develop and document a privacy continuous monitoring strategy.
**Example: 'Monthly PII inventory scan'**
RA-1
[a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] risk assessment policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
2. Procedures to facilitate the implementation of the risk assessment policy and the associated risk assessment controls;
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the risk assessment policy and procedures; and
c. Review and update the current risk assessment:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events].]
**Example: 'Annual risk assessment schedule'**
RA-2
Conduct risk assessments [Assignment: organization-defined frequency] that include:
a. Identifying threats to and vulnerabilities in the system;
**Example: 'Threat intel + Nessus scans'**
b. Determining the likelihood and magnitude of harm from those threats and vulnerabilities;
**Example: 'CVSS scoring + business impact'**
c. Determining risk and risk tolerance;
**Example: 'Risk matrix with heat map'**
d. Implementing controls to reduce or eliminate risk; and
**Example: 'POA&M creation'**
e. Assigning a risk level or risk category to the system.
**Example: 'High/Moderate/Low categorization'**
RA-3
Conduct a risk assessment, including threat modeling, at [Selection (one or more): [Assignment: organization-defined frequency]; the following critical points in the system development life cycle]].
**Example: 'SDLC: design, code complete, pre-prod'**
RA-5
Select vulnerability scanning tools and techniques that:
a. Are tunable to minimize false positives;
**Example: 'Custom Nessus plugin tuning'**
b. Produce detailed reports;
**Example: 'Executive + technical report formats'**
c. Support on-demand and scheduled scans;
**Example: 'Weekly automated + ad-hoc'**
d. Can be integrated into continuous monitoring processes; and
**Example: 'SIEM integration'**
e. Provide an automated means for prioritizing remediation actions.
**Example: 'Risk-based prioritization'**
RA-5(1)
Scan for vulnerabilities in the system and hosted applications [Assignment: organization-defined frequency] and when new vulnerabilities potentially affecting the system are identified and reported.
**Example: 'Daily authenticated scans'**
RA-5(2)
Scan for malicious code [Assignment: organization-defined frequency].
**Example: 'Real-time EDR + daily full scans'**
RA-5(3)
Employ vulnerability scanning tools that include the capability to readily update the information system vulnerabilities to be scanned.
**Example: 'Auto-update Nessus plugins'**
RA-5(4)
Perform periodic scans of the system and real-time scans of files from external sources as the files are downloaded, opened, or executed.
**Example: 'On-access AV scanning'**
RA-5(5)
Employ automated mechanisms to compare the scanned information system vulnerability configuration against the latest component vulnerability information.
**Example: 'SCAP content validation'**
RA-5(6)
Employ automated scanning tools that evaluate application and operating system configuration settings for vulnerabilities.
**Example: 'CIS-CAT Pro compliance scans'**
RA-5(7)
Analyze system vulnerability scan reports [Assignment: organization-defined frequency].
**Example: 'Weekly vulnerability review meeting'**
RA-5(8)
Remediate vulnerabilities in accordance with an organizational assessment of risk.
**Example: '30-day fix for Critical, 90-day High'**
RA-6
Provide a risk response strategy for the system that includes:
a. Risk acceptance, avoidance, mitigation, or transfer; and
**Example: 'Accept low, mitigate high risks'**
b. Approach for monitoring risk over time.
**Example: 'Quarterly risk register update'**
SA-1
[a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] system and services acquisition policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
2. Procedures to facilitate the implementation of the system and services acquisition policy and the associated system and services acquisition controls;
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the system and services acquisition policy and procedures; and
c. Review and update the current system and services acquisition:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events].]
**Example: 'FedRAMP-authorized CSPs only'**
SA-2
a. Include [Assignment: organization-defined security and privacy requirements] in acquisition contracts, solicitations, and procurement specifications;
**Example: 'FISMA compliance clause'**
b. Require [Assignment: organization-defined security and privacy controls] in acquisition contracts, solicitations, and procurement specifications;
**Example: 'FIPS 140-2 validated crypto'**
c. Employ [Assignment: organization-defined processes, methods, and techniques] to monitor third-party-provided products and services for security and privacy controls;
**Example: 'Continuous vendor monitoring'**
d. Include [Assignment: organization-defined supply chain risk management requirements] in acquisition contracts, solicitations, and procurement specifications; and
**Example: 'SBOM requirement'**
e. Include [Assignment: organization-defined requirements for protection of controlled unclassified information] in acquisition contracts, solicitations, and procurement specifications.
**Example: 'CUI marking and handling'**
SA-3
a. Develop a system development life cycle that incorporates information security and privacy requirements and controls;
**Example: 'Secure SDLC with shift-left security'**
b. Include [Assignment: organization-defined system development life cycle phases] in the system development life cycle; and
**Example: 'Initiation, development, deployment, operations'**
c. Document consistent system development life cycle processes and procedures.
**Example: 'DevSecOps pipeline documentation'**
SA-4
a. Require a security and privacy design and implementation plan for external service providers;
**Example: 'Vendor SSP requirement'**
b. Review the security and privacy design and implementation plan for external service providers; and
**Example: 'Monthly vendor control validation'**
c. Require external service providers to implement the security and privacy design and implementation plan.
**Example: 'Contractual control enforcement'**
SA-5
a. Review proposed acquisition of external systems, system components, and services for security and privacy risks;
**Example: 'Vendor risk assessment'**
b. Approve external systems, system components, and services prior to acquisition; and
**Example: 'AO approves all cloud services'**
c. Include security and privacy requirements in acquisition documentation.
**Example: 'SOW includes NIST 800-53 controls'**
SA-8
Apply tailoring guidance for system and service acquisitions.
**Example: 'FedRAMP Moderate baseline'**
SA-9
Require external service providers to comply with organizational security and privacy requirements and employ [Assignment: organization-defined processes, methods, and techniques] to monitor compliance.
**Example: 'Monthly SOC 2 report review'**
SA-10
Develop and document allocation of security and privacy requirements to system components.
**Example: 'Control allocation matrix'**
SA-11
Require developers and suppliers of [Assignment: organization-defined systems or system components] to provide a Software Bill of Materials (SBOM).
**Example: 'CycloneDX SBOM format'**
SA-15
Require the developer of the system, system component, or system service to:
a. Create and implement a final security and privacy configuration for the system, component, or service;
**Example: 'Golden image with STIGs applied'**
b. Protect the confidentiality and integrity of the final security and privacy configuration;
**Example: 'Signed baseline image'**
c. Provide evidence of the final security and privacy configuration; and
**Example: 'SCAP compliance report'**
d. Correct weaknesses or deficiencies in the final security and privacy configuration.
**Example: 'Vendor patch validation'**
SA-17
Accept developer testing and evaluation results when the developer testing and evaluation processes meet [Assignment: organization-defined requirements].
**Example: 'Accept Common Criteria EAL4+ results'**
SA-22
Require the developer of the system, system component, or system service to produce a concept of operations.
**Example: 'Vendor CONOPS document'**
SC-1
[a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] system and communications protection policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
2. Procedures to facilitate the implementation of the system and communications protection policy and the associated system and communications protection controls;
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the system and communications protection policy and procedures; and
c. Review and update the current system and communications protection:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events].]
**Example: 'TLS 1.3 minimum for all communications'**
SC-2
Implement [Assignment: organization-defined cryptographic uses and type of cryptography] requiring FIPS-validated cryptography to protect the confidentiality and integrity of CUI in organizational systems.
**Example: 'AES-256 for all CUI at rest'**
SC-7
Monitor and control communications at the external managed interfaces to the system and at key internal managed interfaces within the system.
**Example: 'Next-gen firewall at internet boundary'**
SC-7(1)
Implement [Assignment: organization-defined filtering techniques] at external and key internal managed interfaces to the system.
**Example: 'Deep packet inspection + IPS'**
SC-7(4)
[Withdrawn: Incorporated into SC-7.]
SC-7(5)
Prevent split tunneling for remote devices.
**Example: 'VPN full tunnel policy'**
SC-7(7)
Implement cryptographic mechanisms to prevent unauthorized modification of externally received information at managed interfaces.
**Example: 'TLS certificate pinning'**
SC-7(8)
Prohibit remote devices from simultaneously establishing non-remote connections with the system and communicating via some other connection to resources in external networks.
**Example: 'No VPN + direct internet'**
SC-7(9)
Implement cryptographic mechanisms to authenticate the following external information sources: [Assignment: organization-defined external information sources].
**Example: 'DNSSEC for authoritative servers'**
SC-7(10)
Practice least functionality by only providing information system boundary protection functionality for the following: [Assignment: organization-defined missions and business functions].
**Example: 'Finance VLAN cannot access HR systems'**
SC-7(11)
Separate user functionality from system management functionality.
**Example: 'Out-of-band management network'**
SC-7(12)
Separate information producer and consumer communications channels.
**Example: 'Unidirectional gateway for classified data'**
SC-7(13)
Separate user and system management communications channels.
**Example: 'Admin VLAN isolated from user VLAN'**
SC-7(14)
Implement subnetworks for publicly accessible system components that are [Selection: physically; logically] separated from internal organizational networks.
**Example: 'DMZ with no internal routing'**
SC-7(15)
Deny communications with the following external systems or system components by default: [Assignment: organization-defined external systems or system components].
**Example: 'Default deny all outbound'**
SC-7(16)
Control network communications traffic entering organizational systems destined for [Assignment: organization-defined information resources] using [Assignment: organization-defined controls].
**Example: 'WAF protecting web applications'**
SC-7(17)
Control network communications traffic leaving organizational systems destined for [Assignment: organization-defined external systems or system components] using [Assignment: organization-defined controls].
**Example: 'DLP gateway for outbound traffic'**
SC-7(18)
Control network communications traffic between organizational components using [Assignment: organization-defined controls].
**Example: 'Microsegmentation with NSX'**
SC-7(19)
Implement cryptographic mechanisms to protect the confidentiality and integrity of information transmitted across system protection boundaries.
**Example: 'IPsec VPN between data centers'**
SC-7(20)
Implement cryptographic mechanisms to prevent unauthorized modification of information during transmission across system protection boundaries.
**Example: 'HMAC-SHA256 message authentication'**
SC-7(21)
Enforce [Assignment: organization-defined limitations] on the number of network connections between system components.
**Example: 'Rate limiting between microservices'**
SC-7(22)
Prevent network communications traffic destined for [Assignment: organization-defined information resources] from being routed through [Assignment: organization-defined prohibited systems or system components].
**Example: 'No traffic through employee laptops'**
SC-7(23)
Prevent [Assignment: organization-defined communications traffic] from being routed through [Assignment: organization-defined systems or system components].
**Example: 'Block C2 traffic patterns'**
SC-7(24)
Monitor communications at the external managed network interfaces to the system to discover unauthorized connections.
**Example: 'Continuous network discovery'**
SC-7(25)
Employ [Assignment: organization-defined mechanisms] to protect the confidentiality and integrity of information transmitted across and between [Assignment: organization-defined systems or system components].
**Example: 'mTLS between Kubernetes pods'**
SC-7(26)
Prohibit the use of [Assignment: organization-defined communications protocols] except when required for [Assignment: organization-defined mission or operational requirements].
**Example: 'Telnet prohibited, SSH required'**
SC-7(27)
Implement a managed interface for each functional capability required for system operation.
**Example: 'API gateway for all services'**
SC-7(28)
Implement [Assignment: organization-defined controls] to provide protection equivalent to the controls for the system at [Assignment: organization-defined managed interfaces].
**Example: 'Same firewall rules at all boundaries'**
SC-8
Implement cryptographic mechanisms to protect the confidentiality of CUI during transmission unless otherwise protected by alternative physical safeguards.
**Example: 'HTTPS with HSTS everywhere'**
SC-12
Prohibit remote activation of collaborative computing devices and provide indication of devices in use to users present at the device.
**Example: 'Microphone LED indicator'**
SC-13
Terminate collaborative computing sessions when [Assignment: organization-defined circumstances].
**Example: '30-minute inactivity timeout'**
SC-17
Provide the capability for session authenticity using the following mechanisms: [Assignment: organization-defined session authentication mechanisms].
**Example: 'WebAuthn FIDO2 tokens'**
SC-20
Implement cryptographic mechanisms to protect CUI in storage except for the following exempted systems: [Assignment: organization-defined exempted systems].
**Example: 'RAM-only analytics systems'**
SC-23
Deny network communications traffic by default and allow network communications traffic by exception (i.e., deny all, permit by exception).
**Example: 'Zero trust network access model'**
SC-28
Protect the confidentiality and integrity of CUI on [Assignment: organization-defined types of mobile devices].
**Example: 'Intune MDM with app protection'**
SC-28(1)
Prohibit the use of binary or machine-executable code from sources with limited or no warranty without the provision of source code.
**Example: 'No unsigned mobile apps'**
SC-39
Terminate processes, kill threads, and isolate system components when [Assignment: organization-defined indicators of compromise].
**Example: 'EDR automatic response'**
SC-40
Implement a diverse set of [Assignment: organization-defined cryptographic technologies] to support distributed transaction processing.
**Example: 'Quantum-resistant + classical crypto'**
SC-41
Implement [Assignment: organization-defined cryptographic operations] using cryptographic modules that meet [Assignment: organization-defined requirements].
**Example: 'FIPS 140-2 Level 3 HSM'**
SC-43
Implement controls to protect communications authentication from [Assignment: organization-defined man-in-the-middle attacks].
**Example: 'Certificate transparency logs'**
SC-44
Implement integrity-based session authenticity mechanisms.
**Example: 'HTTP Digest Authentication'**
SC-45
Use internal system clocks to generate time stamps for [Assignment: organization-defined audit records].
**Example: 'NTP synchronized logging'**
SC-46
Prevent unauthorized exfiltration of information via [Assignment: organization-defined methods].
**Example: 'DLP blocks email with PII'**
SI-1
[a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] system and information integrity policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
2. Procedures to facilitate the implementation of the system and information integrity policy and the associated system and information integrity controls;
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the system and information integrity policy and procedures; and
c. Review and update the current system and information integrity:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events].]
**Example: 'File integrity monitoring required'**
SI-2
Employ file integrity monitoring tools to detect unauthorized changes to [Assignment: organization-defined system files].
**Example: 'Tripwire on /etc and /bin'**
SI-2(1)
Monitor system security functions to detect tampering and unauthorized changes.
**Example: 'Auditd monitoring SELinux policy'**
SI-2(2)
Provide automated notification of [Assignment: organization-defined file integrity violations].
**Example: 'Email + Slack alerts for FIM violations'**
SI-2(3)
Configure file integrity monitoring tools to:
a. Perform scans [Assignment: organization-defined frequency]; and
**Example: 'Real-time + hourly baseline scans'**
b. [Selection (one or more): alert; report] violations to [Assignment: organization-defined personnel or roles].
**Example: 'Page on-call for critical changes'**
SI-3
Identify and protect against [Assignment: organization-defined malicious code] using [Assignment: organization-defined malicious code protection mechanisms].
**Example: 'CrowdStrike Falcon EDR'**
SI-3(1)
Employ automated mechanisms to determine the state of [Assignment: organization-defined system components] with regard to malicious code protection.
**Example: 'AV compliance dashboard'**
SI-3(2)
Configure malicious code protection mechanisms to:
a. Perform periodic scans of the system [Assignment: organization-defined frequency] and real-time scans of files from external sources as the files are downloaded, opened, or executed;
**Example: 'On-access + daily full scan'**
b. [Selection (one or more): update malicious code protection mechanisms; perform [Assignment: organization-defined actions]] when new releases are available in accordance with organizational configuration management policy and procedures;
**Example: 'Auto-update signatures daily'**
c. [Selection (one or more): alert; block; quarantine] malicious code; and
**Example: 'Auto-quarantine + SOC alert'**
d. Configure malicious code protection mechanisms to employ the following capabilities: [Assignment: organization-defined capabilities].
**Example: 'Sandbox analysis + behavioral detection'**
SI-3(3)
Employ malicious code protection mechanisms for [Assignment: organization-defined mobile devices].
**Example: 'MobileIron AV for BYOD'**
SI-3(4)
Employ [Assignment: organization-defined malicious code protection mechanisms] at [Assignment: organization-defined system entry and exit points].
**Example: 'Email gateway + web proxy AV'**
SI-3(5)
Employ [Assignment: organization-defined malicious code analysis techniques] to identify unknown malicious code.
**Example: 'Cuckoo Sandbox detonation'**
SI-3(6)
Utilize [Assignment: organization-defined malicious code protection mechanisms] that employ signatures to identify known malicious code.
**Example: 'YARA rules for malware detection'**
SI-3(7)
Employ [Assignment: organization-defined malicious code protection mechanisms] that block execution of known malicious code.
**Example: 'Application whitelisting'**
SI-4
Monitor the system to detect:
a. Attacks and indicators of potential attacks; and
**Example: 'SIEM threat hunting'**
b. Unauthorized local, network, and remote connections.
**Example: 'Netflow anomaly detection'**
SI-4(1)
Employ analysis mechanisms to analyze events for indicators of compromise.
**Example: 'UEBA behavioral analytics'**
SI-4(2)
Employ [Assignment: organization-defined automated mechanisms] to support near-real-time analysis of events.
**Example: 'Splunk SOAR playbooks'**
SI-4(3)
[Withdrawn: Incorporated into SI-4.]
SI-4(4)
Employ [Assignment: organization-defined tools and techniques] to continuously monitor for attacks.
**Example: 'Continuous threat hunting'**
SI-4(5)
Employ [Assignment: organization-defined automated mechanisms] to:
a. Collect and correlate information from multiple sources; and
**Example: 'SOAR correlation engine'**
b. Alert [Assignment: organization-defined personnel or roles].
**Example: 'Tiered alerting escalation'**
SI-4(6)
Employ [Assignment: organization-defined monitoring tools] to monitor connections between [Assignment: organization-defined system components].
**Example: 'Zeek network monitoring'**
SI-4(7)
Employ [Assignment: organization-defined monitoring capabilities] to detect [Assignment: organization-defined conditions requiring vetting of system components].
**Example: 'Memory forensics for implants'**
SI-4(8)
Alert designated organizational officials using [Assignment: organization-defined automated mechanisms] within [Assignment: organization-defined time period] of detection of attack-related indicators.
**Example: '5-minute critical alert SLA'**
SI-4(9)
Provide [Assignment: organization-defined capabilities] to adjust the level of monitoring activity based on [Assignment: organization-defined threat intelligence].
**Example: 'Elevated monitoring during threat campaigns'**
SI-4(10)
Employ [Assignment: organization-defined monitoring systems] that integrate with threat intelligence feeds.
**Example: 'MISP threat intel integration'**
SI-4(11)
Employ [Assignment: organization-defined capabilities] to automatically respond to detected indications of compromise.
**Example: 'Auto-isolate compromised endpoints'**
SI-4(12)
Employ [Assignment: organization-defined capabilities] to support dynamic reconfiguration in response to attacks.
**Example: 'Runtime application self-protection'**
SI-4(13)
Employ [Assignment: organization-defined capabilities] to detect and respond to unauthorized mobile device connections.
**Example: 'NAC rogue device detection'**
SI-4(14)
Employ [Assignment: organization-defined capabilities] to detect and respond to supply chain attacks.
**Example: 'SBOM continuous monitoring'**
SI-4(15)
Employ [Assignment: organization-defined capabilities] to detect and respond to cloud service provider incidents.
**Example: 'AWS GuardDuty integration'**
SI-4(16)
Employ [Assignment: organization-defined capabilities] to detect and respond to attacks by advanced persistent threat actors.
**Example: 'APT hunting with MITRE ATT&CK'**
SI-4(17)
Employ [Assignment: organization-defined capabilities] to detect and respond to attacks against operational technology.
**Example: 'OT-specific IDS/IPS'**
SI-4(18)
Employ [Assignment: organization-defined capabilities] to detect and respond to insider threat activity.
**Example: 'UEBA for anomalous behavior'**
SI-5
Identify and document security weaknesses and deficiencies in the system using [Assignment: organization-defined automated and manual processes].
**Example: 'Weekly vulnerability reports'**
SI-5(1)
Identify and document security weaknesses and deficiencies using [Assignment: organization-defined sources of threat information].
**Example: 'CISA KEV + vendor advisories'**
SI-5(2)
Review identified security weaknesses and deficiencies [Assignment: organization-defined frequency].
**Example: 'Daily vulnerability prioritization'**
SI-6
Monitor organizational systems, including inbound and outbound communications traffic, to identify attacks and indicators of potential attacks.
**Example: '24x7 SOC monitoring'**
SI-6(1)
Test malicious code to determine [Assignment: organization-defined characteristics of malicious code].
**Example: 'Static + dynamic malware analysis'**
SI-6(2)
Employ [Assignment: organization-defined intrusion detection and prevention capabilities].
**Example: 'Snort IPS signatures'**
SI-6(3)
Identify and mitigate [Assignment: organization-defined types of supply chain attacks].
**Example: 'SolarWinds-style compromise detection'**
SI-7
Identify and correct software, firmware, and hardware flaws that could result in [Assignment: organization-defined vulnerabilities].
**Example: 'Patch management program'**
SI-7(1)
Check the integrity of [Assignment: organization-defined software, firmware, and hardware].
**Example: 'SBOM integrity verification'**
SI-7(2)
Remediate [Assignment: organization-defined vulnerabilities] in accordance with [Assignment: organization-defined operational requirements].
**Example: '30/60/90 day remediation SLA'**
SI-7(3)
Employ [Assignment: organization-defined vulnerability protection mechanisms].
**Example: 'ASLR + DEP enabled'**
SI-7(4)
[Withdrawn: Incorporated into SR-9.]
SI-8
Screen email and web content for malicious code using [Assignment: organization-defined malicious code screening techniques].
**Example: 'Proofpoint URL sandbox'**
SI-8(1)
[Withdrawn: Incorporated into PL-9.]
SI-8(2)
Automatically update spam protection mechanisms [Assignment: organization-defined frequency].
**Example: 'Hourly signature updates'**
SI-8(3)
Implement spam protection mechanisms with a learning capability to more effectively identify legitimate communications traffic.
**Example: 'AI-driven spam filtering'**
SI-10
Check the validity of the following information inputs: [Assignment: organization-defined information inputs to the system].
**Example: 'SQL injection prevention'**
SI-10(1)
"(a) Provide a manual override capability for input validation of the following information inputs: [Assignment: organization-defined inputs defined in the base control (SI-10)];
**Example: 'Admin override for business rules'**
(b) Restrict the use of the manual override capability to only [Assignment: organization-defined authorized individuals]; and
**Example: 'Dual auth for overrides'**
(c) Audit the use of the manual override capability."
**Example: 'All overrides logged in SIEM'**
SI-10(2)
Review and resolve input validation errors within [Assignment: organization-defined time period].
**Example: '4-hour SLA for validation failures'**
SI-10(3)
Verify that the system behaves in a predictable and documented manner when invalid inputs are received.
**Example: 'Fail-safe input rejection'**
SI-10(4)
Account for timing interactions among system components in determining appropriate responses for invalid inputs.
**Example: 'Race condition protection'**
SI-10(5)
Restrict the use of information inputs to [Assignment: organization-defined trusted sources] and/or [Assignment: organization-defined formats].
**Example: 'XML schema validation'**
SI-10(6)
Prevent untrusted data injections.
**Example: 'Parameterized queries only'**
SI-11
"a. Generate error messages that provide information necessary for corrective actions without revealing information that could be exploited; and
**Example: 'Generic "invalid input" message'**
b. Reveal error messages only to [Assignment: organization-defined personnel or roles]."
**Example: 'Admin console only for detailed errors'**
SI-12
Manage and retain information within the system and information output from the system in accordance with applicable laws, executive orders, directives, regulations, policies, standards, guidelines and operational requirements.
**Example: '7-year retention for financial records'**
SI-12(1)
Limit personally identifiable information being processed in the information life cycle to the following elements of personally identifiable information: [Assignment: organization-defined elements of personally identifiable information].
**Example: 'Last 4 SSN only'**
SI-12(2)
Use the following techniques to minimize the use of personally identifiable information for research, testing, or training: [Assignment: organization-defined techniques].
**Example: 'Synthetic test data generation'**
SI-12(3)
Use the following techniques to dispose of, destroy, or erase information following the retention period: [Assignment: organization-defined techniques].
**Example: 'Secure delete with sdelete'**
SI-13
"a. Determine mean time to failure (MTTF) for the following system components in specific environments of operation: [Assignment: organization-defined system components]; and
**Example: 'SSD MTTF in data center temp'**
b. Provide substitute system components and a means to exchange active and standby components in accordance with the following criteria: [Assignment: organization-defined MTTF substitution criteria]."
**Example: 'Replace at 80% MTTF'**
SI-13(1)
Take system components out of service by transferring component responsibilities to substitute components no later than [Assignment: organization-defined fraction or percentage] of mean time to failure.
**Example: 'Hot-swap at 90% MTTF'**
SI-9
[Withdrawn: Incorporated into AC-2, AC-3, AC-5, and AC-6.]
SI-13(3)
Manually initiate transfers between active and standby system components when the use of the active component reaches [Assignment: organization-defined percentage] of the mean time to failure.
**Example: 'Manual failover at 85% MTTF'**
SI-13(4)
"If system component failures are detected:
(a) Ensure that the standby components are successfully and transparently installed within [Assignment: organization-defined time period]; and
**Example: '30-second failover SLA'**
(b) [Selection (one or more): Activate [Assignment: organization-defined alarm]; Automatically shut down the system; [Assignment: organization-defined action]]."
**Example: 'Page on-call + graceful shutdown'**
SI-13(5)
Provide [Selection: real-time; near real-time] [Assignment: organization-defined failover capability] for the system.
**Example: 'Synchronous replication with <1s RPO'**
SI-14
Implement non-persistent [Assignment: organization-defined system components and services] that are initiated in a known state and terminated [Selection (one or more): upon end of session of use; periodically at [Assignment: organization-defined frequency]].
**Example: 'Container restart every 24 hours'**
SI-14(1)
Obtain software and data employed during system component and service refreshes from the following trusted sources: [Assignment: organization-defined trusted sources].
**Example: 'Official Docker Hub images only'**
SI-14(2)
"(a) [Selection: Refresh [Assignment: organization-defined information][Assignment: organization-defined frequency]; Generate [Assignment: organization-defined information] on demand]; and
**Example: 'Daily ephemeral container refresh'**
(b) Delete information when no longer needed."
**Example: 'Auto-delete temp files'**
SI-14(3)
Establish connections to the system on demand and terminate connections after [Selection: completion of a request; a period of non-use].
**Example: 'Serverless functions auto-scale'**
SI-15
Validate information output from the following software programs and/or applications to ensure that the information is consistent with the expected content: [Assignment: organization-defined software programs and/or applications].
**Example: 'Checksum validation for reports'**
SI-16
Implement the following controls to protect the system memory from unauthorized code execution: [Assignment: organization-defined controls].
**Example: 'ASLR + W^X memory protection'**
SI-17
Implement the indicated fail-safe procedures when the indicated failures occur: [Assignment: organization-defined list of failure conditions and associated fail-safe procedures].
**Example: 'Power failure → graceful shutdown'**
SI-18
"a. Check the accuracy, relevance, timeliness, and completeness of personally identifiable information across the information life cycle [Assignment: organization-defined frequency]; and
**Example: 'Monthly PII validation scan'**
b. Correct or delete inaccurate or outdated personally identifiable information."
**Example: 'Automated data cleansing'**
SI-18(1)
Correct or delete personally identifiable information that is inaccurate or outdated, incorrectly determined regarding impact, or incorrectly de-identified using [Assignment: organization-defined automated mechanisms].
**Example: 'Data quality firewall'**
SI-18(2)
Employ data tags to automate the correction or deletion of personally identifiable information across the information life cycle within organizational systems.
**Example: 'PII metadata tagging'**
SI-18(3)
Collect personally identifiable information directly from the individual.
**Example: 'Self-service profile update portal'**
SI-18(4)
Correct or delete personally identifiable information upon request by individuals or their designated representatives.
**Example: 'DSAR portal with 30-day response'**
SI-18(5)
Notify [Assignment: organization-defined recipients of personally identifiable information] and individuals that the personally identifiable information has been corrected or deleted.
**Example: 'Confirmation email after DSAR'**
SI-19
"a. Remove the following elements of personally identifiable information from datasets: [Assignment: organization-defined elements of personally identifiable information]; and
**Example: 'Remove full SSN, keep last 4'**
b. Evaluate [Assignment: organization-defined frequency] for effectiveness of de-identification."
**Example: 'Quarterly re-identification risk assessment'**
SI-19(1)
De-identify the dataset upon collection by not collecting personally identifiable information.
**Example: 'Aggregate statistics only'**
SI-19(2)
Prohibit archiving of personally identifiable information elements if those elements in a dataset will not be needed after the dataset is archived.
**Example: 'Strip PII before cold storage'**
SI-19(3)
Remove personally identifiable information elements from a dataset prior to its release if those elements in the dataset do not need to be part of the data release.
**Example: 'Anonymize before public dataset'**
SI-19(4)
Remove, mask, encrypt, hash, or replace direct identifiers in a dataset.
**Example: 'SHA-256 hash of email addresses'**
SI-19(5)
Manipulate numerical data, contingency tables, and statistical findings so that no individual or organization is identifiable in the results of the analysis.
**Example: 'Differential privacy noise addition'**
SI-19(6)
Prevent disclosure of personally identifiable information by adding non-deterministic noise to the results of mathematical operations before the results are reported.
**Example: 'Local differential privacy'**
SI-19(7)
Perform de-identification using validated algorithms and software that is validated to implement the algorithms.
**Example: 'ARX anonymization tool'**
SI-19(8)
Perform a motivated intruder test on the de-identified dataset to determine if the identified data remains or if the de-identified data can be re-identified.
**Example: 'K-anonymity validation testing'**
SI-20
Embed data or capabilities in the following systems or system components to determine if organizational data has been exfiltrated or improperly removed from the organization: [Assignment: organization-defined systems or system components].
**Example: 'Data watermarking in documents'**
SI-21
Refresh [Assignment: organization-defined information] at [Assignment: organization-defined frequencies] or generate the information on demand and delete the information when no longer needed.
**Example: 'Ephemeral session data'**
SI-22
"a. Identify the following alternative sources of information for [Assignment: organization-defined essential functions and services]: [Assignment: organization-defined alternative information sources]; and
**Example: 'Backup NTP servers'**
b. Use an alternative information source for the execution of essential functions or services on [Assignment: organization-defined systems or system components] when the primary source of information is corrupted or unavailable."
**Example: 'Fallback to local clock if NTP fails'**
SI-23
"Based on [Assignment: organization-defined circumstances]:
a. Fragment the following information: [Assignment: organization-defined information]; and
**Example: 'Secret share crypto keys'**
b. Distribute the fragmented information across the following systems or system components: [Assignment: organization-defined systems or system components]."
**Example: 'Shamir's Secret Sharing across 3 HSMs'**
SR-1
"a. Develop, document, and disseminate to [Assignment: organization-defined personnel or roles]:
1. [Selection (one or more): Organization-level; Mission/business process-level; System-level] supply chain risk management policy that:
(a) Addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance; and
**Example: 'Vendor risk management program'**
(b) Is consistent with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines; and
2. Procedures to facilitate the implementation of the supply chain risk management policy and the associated supply chain risk management controls;
**Example: 'Third-party risk assessment process'**
b. Designate an [Assignment: organization-defined official] to manage the development, documentation, and dissemination of the supply chain risk management policy and procedures; and
**Example: 'Supply Chain Risk Manager'**
c. Review and update the current supply chain risk management:
1. Policy [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]; and
**Example: 'Annually and after EO updates'**
2. Procedures [Assignment: organization-defined frequency] and following [Assignment: organization-defined events]."
**Example: 'After SolarWinds incident'**
SR-2
"a. Develop a plan for managing supply chain risks associated with the research and development, design, manufacturing, acquisition, delivery, integration, operations and maintenance, and disposal of the following systems, system components or system services: [Assignment: organization-defined systems, system components, or system services];
**Example: 'Cloud platform SCRM plan'**
b. Review and update the supply chain risk management plan [Assignment: organization-defined frequency] or as required, to address threat, organizational or environmental changes; and
**Example: 'Quarterly threat landscape review'**
c. Protect the supply chain risk management plan from unauthorized disclosure and modification."
**Example: 'Encrypted SharePoint with RBAC'**
SR-2(1)
Establish a supply chain risk management team consisting of [Assignment: organization-defined personnel, roles, and responsibilities] to lead and support the following SCRM activities: [Assignment: organization-defined supply chain risk management activities].
**Example: 'CISO + Procurement + Legal SCRM team'**
SR-3
"a. Establish a process or processes to identify and address weaknesses or deficiencies in the supply chain elements and processes of [Assignment: organization-defined system or system component] in coordination with [Assignment: organization-defined supply chain personnel];
**Example: 'Vendor questionnaire + onsite audit'**
b. Employ the following controls to protect against supply chain risks to the system, system component, or system service and to limit the harm or consequences from supply chain-related events: [Assignment: organization-defined supply chain controls]; and
**Example: 'Code signing + SBOM verification'**
c. Document the selected and implemented supply chain processes and controls in [Selection: security and privacy plans; supply chain risk management plan; [Assignment: organization-defined document]]."
**Example: 'Vendor risk register'**
SR-3(1)
Employ a diverse set of sources for the following system components and services: [Assignment: organization-defined system components and services].
**Example: 'Multi-vendor cloud strategy'**
SR-3(2)
Employ the following controls to limit harm from potential adversaries identifying and targeting the organizational supply chain: [Assignment: organization-defined controls].
**Example: 'Vendor name obfuscation'**
SR-3(3)
Ensure that the controls included in the contracts of prime contractors are also included in the contracts of subcontractors.
**Example: 'Flow-down clauses in all agreements'**
SR-4
Document, monitor, and maintain valid provenance of the following systems, system components, and associated data: [Assignment: organization-defined systems, system components, and associated data].
**Example: 'Blockchain-based component tracking'**
SR-4(1)
Establish and maintain unique identification of the following supply chain elements, processes, and personnel associated with the identified system and critical system components: [Assignment: organization-defined supply chain elements, processes, and personnel associated with organization-defined systems and critical system components].
**Example: 'UUID for every firmware version'**
SR-4(2)
Establish and maintain unique identification of the following systems and critical system components for tracking through the supply chain: [Assignment: organization-defined systems and critical system components].
**Example: 'CAGE code + part number tracking'**
SR-4(3)
Employ the following controls to validate that the system or system component received is genuine and has not been altered: [Assignment: organization-defined controls].
**Example: 'PGP signature verification'**
SR-4(4)
Employ [Assignment: organization-defined controls] and conduct [Assignment: organization-defined analysis] to ensure the integrity of the system and system components by validating the internal composition and provenance of critical or mission-essential technologies, products, and services.
**Example: 'Binary SBOM analysis with in-toto'**
SR-5
Employ the following acquisition strategies, contract tools, and procurement methods to protect against, identify, and mitigate supply chain risks: [Assignment: organization-defined acquisition strategies, contract tools, and procurement methods].
**Example: 'OTAs + lowest risk vendors'**
SR-5(1)
Employ the following controls to ensure an adequate supply of [Assignment: organization-defined critical system components]: [Assignment: organization-defined controls].
**Example: '6-month spare parts inventory'**
SR-5(2)
Assess the system, system component, or system service prior to selection, acceptance, modification, or update.
**Example: 'Pre-acceptance pentest required'**
SR-6
Assess and review the supply chain-related risks associated with suppliers or contractors and the system, system component, or system service they provide [Assignment: organization-defined frequency].
**Example: 'Annual vendor risk assessment'**
SR-6(1)
Employ [Selection (one or more): organizational analysis; independent third-party analysis; organizational testing; independent third-party testing] of the following supply chain elements, processes, and actors associated with the system, system component, or system service: [Assignment: organization-defined supply chain elements, processes, and actors].
**Example: '3rd party SOC 2 Type II audit'**
SR-7
Employ the following Operations Security (OPSEC) controls to protect supply chain-related information for the system, system component, or system service: [Assignment: organization-defined Operations Security (OPSEC) controls].
**Example: 'Vendor contract details classified'**
SR-8
Establish agreements and procedures with entities involved in the supply chain for the system, system component, or system service for the [Selection (one or more): notification of supply chain compromises; results of assessments or audits; [Assignment: organization-defined information]].
**Example: '72-hour breach notification SLA'**
SR-9
Implement a tamper protection program for the system, system component, or system service.
**Example: 'Hardware root of trust'**
SR-9(1)
Employ anti-tamper technologies, tools, and techniques throughout the system development life cycle.
**Example: 'Secure boot chain'**
SR-10
Inspect the following systems or system components [Selection (one or more): at random; at [Assignment: organization-defined frequency], upon [Assignment: organization-defined indications of need for inspection]] to detect tampering: [Assignment: organization-defined systems or system components].
**Example: 'Monthly random HSM inspection'**
SR-11
"a. Develop and implement anti-counterfeit policy and procedures that include the means to detect and prevent counterfeit components from entering the system; and
**Example: 'Holographic authenticity labels'**
b. Report counterfeit system components to [Selection (one or more): source of counterfeit component; [Assignment: organization-defined external reporting organizations]; [Assignment: organization-defined personnel or roles]]."
**Example: 'Report to GIDEP database'**
SR-11(1)
Train [Assignment: organization-defined personnel or roles] to detect counterfeit system components (including hardware, software, and firmware).
**Example: 'Annual counterfeit awareness training'**
SR-11(2)
Maintain configuration control over the following system components awaiting service or repair and serviced or repaired components awaiting return to service: [Assignment: organization-defined system components].
**Example: 'Quarantine repaired parts'**
SR-11(3)
Scan for counterfeit system components [Assignment: organization-defined frequency].
**Example: 'X-ray inspection of critical chips'**
SR-12
Dispose of [Assignment: organization-defined data, documentation, tools, or system components] using the following techniques and methods: [Assignment: organization-defined techniques and methods].
**Example: 'Pulverize high-value hardware'**