Hooray for Hollywood! – Hackers Hold Healthcare Hostage
Hackers Hold Hollywood Healthcare Hostage

Hollywood Presbyterian Medical Center paid a $17,000 ransom in bitcoin to hackers who seized control of the hospital’s computer systems holding them a healthcare hostage. The cyber assault on Hollywood Presbyterian occurred Feb. 5, 2016, when hackers using malware infected the institution’s computers, preventing hospital staff from being able to communicate from those devices.
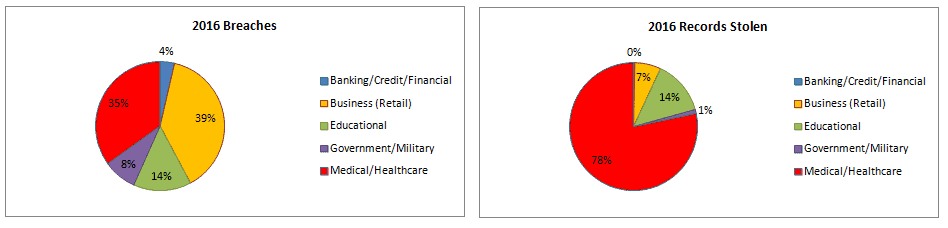
In 2015 the most cyber crime bloodletting occurred in healthcare and 2016 is already trending to the same trajectory. Cyber security providers out there offer Band-aid solutions but what the healthcare industry needs is a cure. Continuum GRC has the solution that can inoculate your organization against these threats, preventing hackers from holding your patients and your business a healthcare hostage.
What could Hollywood Presbyterian Medical Center have done differently to have avoided being a victim to hackers? For starters, they could have taken a proactive approach and identified where their risks were, but instead they took a reactive approach, and now their business has been damaged. The cyber security experts at Continuum GRC know that when you take a proactive approach to security, compliance, audit and governance, you eliminate the potential for sending your business to the emergency room or worse yet, the morgue!
The following steps are proven to help:
- Conduct a systematic standards-based risk assessment of your organization
- Complete an internal controls assessment using industry frameworks to guide you through the process
- Proactively review all threat vectors eliminating them before criminals exploit them
Sound daunting? We know it is and that is why Continuum GRC takes the guesswork and complexity out of the assessment and certification process. Subscribe to the best tools that are guaranteed to help you avoid becoming a victim to hackers.
Check this out for yourself by contacting us at 1-888-896-6207 or just sign-up for a free trial.
 It is always rewarding when cyber security and cyber forensics protect the innocent.
It is always rewarding when cyber security and cyber forensics protect the innocent.