Defeating Cyber Security Deficits with a 1-2 Punch
Steve Morgan, a professional acquaintance who writes about cyber security for Forbes published One Million Cybersecurity Job Openings In 2016 and revealed some jaw-dropping statistics concerning the growing deficit in hiring qualified cyber security employees. To make matters worse, this chasm is exacerbated by the explosion of corporate breaches impacting and even decimating businesses in financials, education, business, government and especially healthcare.

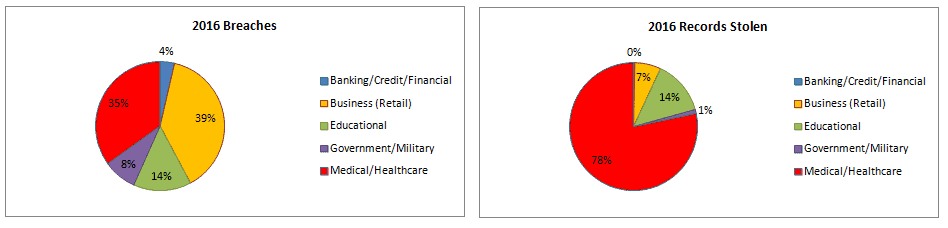
In 2015, there were nearly 170,000,000 records exposed and that astronomical figure is just what we have been able to catalog. When cyber criminals run wild on your networks on average for 200 days before you know about it, that number most assuredly falls short of the actual impact. Cyber security breaches are increasing with a magnitude that is overwhelming.
Who is going to help turn the tide against these alarming trends? A recent report revealed that “More than 209,000 cybersecurity jobs in the U.S. are unfilled, and postings are up 74% over the past five years, according to a Peninsula Press (a project of the Stanford University Journalism Program) 2015 analysis of numbers from the Bureau of Labor Statistics.” It is pretty clear that while there currently is not enough talent to go around; this is only getting exponentially worse!
The upside for people who currently are in the cyber security profession or those who want to get into it means that:
- You are going to make about 9% more than other IT workers do at current compensation rates.
- There is a 36.5% growth rate in cyber security career fields which is not sustainable for companies and puts existing employees in higher demand to the highest bidder.
Another report included “A report from Cisco puts the global figure at one million cybersecurity job openings. The demand for the (cybersecurity) workforce is expected to rise to 6 million (globally) by 2019, with a projected shortfall of 1.5 million” stated Michael Brown, CEO at Symantec, the world’s largest security software vendor.” This only turns up the anxiety level on companies who are scrambling to avoid being the “breach du jour”.
Compounding matters are that there is a significant increase in regulatory and compliance requirements across all industries. Every compliance framework out there went through major overhauls in 2015. In some cases as is the case for the SSAE 16; doubled in complexity. The situation just got more expensive and complex.
The only clear answers for businesses who want to remain viable in the global cyber threatscape come in the form of increased efficiencies and leveraged resources. Two of the best solutions that have emerged to address these challenges are:

Retain a Cybervisor®
Why should only big business be able to afford world class technology security executive representation? You retain attorneys and accountants to perform complex tasks and represent you; retain technology security executive services and subject matter experts just the same! Even with 7% to 15% average annual increases by cyber security providers it is still less than 50% of the cost increases associated with employees.
Retaining the help from dedicated and verifiable cyber security experts costs less than the expense of hiring just one (1) cyber security employee. And yes, that was a plural not singular expert. With professional Cybervisor services companies get the expertise of many seasoned experts who collaborate and stand together to support their clients.
 Automation is Your Friend
Automation is Your Friend
It’s time to work smarter and not harder! By utilizing automated cyber security and GRC tools, we have discovered that employees are so much more efficient and effective. In fact utilizing a tool like ITAM IT audit software consistently makes the cyber security, GRC assessments and reporting processes a whopping 180% more efficient on average. When time is money, ITAM IT audit software is like getting three (3) dedicated cyber security employees for less than the cost of one (1).
This concept of working smarter not harder applies to all cyber security and GRC service providers world-wide. Why pay for your current third-party provider’s overhead and antiquated assessment processes when you can significantly reduce your expenses and increase your profit margins simply by using a modern, intelligently designed cutting-edge GRC tool like ITAM IT audit software?
ITAM IT audit software is an intelligently designed GRC tool that gets you from zero to compliance in record time by eliminating the audit anarchy you are accustomed to. There is a superior solution to this old-school problem and ITAM IT audit software is keystone to that solution.