Continuum GRC unveils the next generation of cyber-crime prevention for organizations with NIST and SEC, NFA compliance requirements in concert with the Cyber Security Act of 2015.
Continuum GRC released the next generation antidote to fight cyber crime, compliance failures, corporate fraud and criminal cyber-misconduct with the IT Audit Machine (ITAM IT audit software).

Considered to be the best assessment tool for governance, risk and compliance (GRC) in the global business community in compliance with the Cyber Security Act of 2015, this next generation of ITAM IT audit software ups the ante by managing big data and frameworks with virtually endless possibilities. These new enterprise capabilities coupled with the already powerful analytic and logic features are a technological force to be reckoned with.
Congress & President Obama recently enacted a cybersecurity piece of legislation known as the “Cybersecurity Act of 2015” which is designed to ensure that public companies “provide a basic amount of information about the degree to which a firm is protecting the economic and financial interests of the firm from cyber-attacks” using guidance from the SEC, NFA and the National Institute of Standards and Technology (NIST).
In addition, the Cyber Security Act of 2015 strengthens and prioritizes cybersecurity at publicly traded companies by encouraging the disclosure of cybersecurity expertise, or lack thereof, on corporate boards at these companies. This legislation requires companies to disclose – in their SEC, NFA filings – whether they have a director who is a “cybersecurity expert” – and if not, why having this expertise on the board isn’t necessary because of other cybersecurity steps taken by the company.
The Cyber Security Act of 2015 would require the SEC, NFA and the National Institute of Standards and Technology (NIST) to provide guidance on the qualifications necessary to be a cybersecurity expert.
Michael Peters, CEO of Continuum GRC said “The IT Audit Machine NIST and SEC, NFA compliance assessment modules are just one of the many innovations from Continuum GRC that really sets us apart from other cyberspace Security, governance, risk and compliance software firms.”
The top sources for learning more about the threatscape for cyber security since 2005 has been the Privacy Rights Clearinghouse and a similar industry analysis resource is the Identity Theft Resource Center who have only been tracking cyber security breach statistics since 2014. Continuum GRC has been leading the charge since 2000 when the company introduced the concept of Proactive Cyber Security™ to the world.
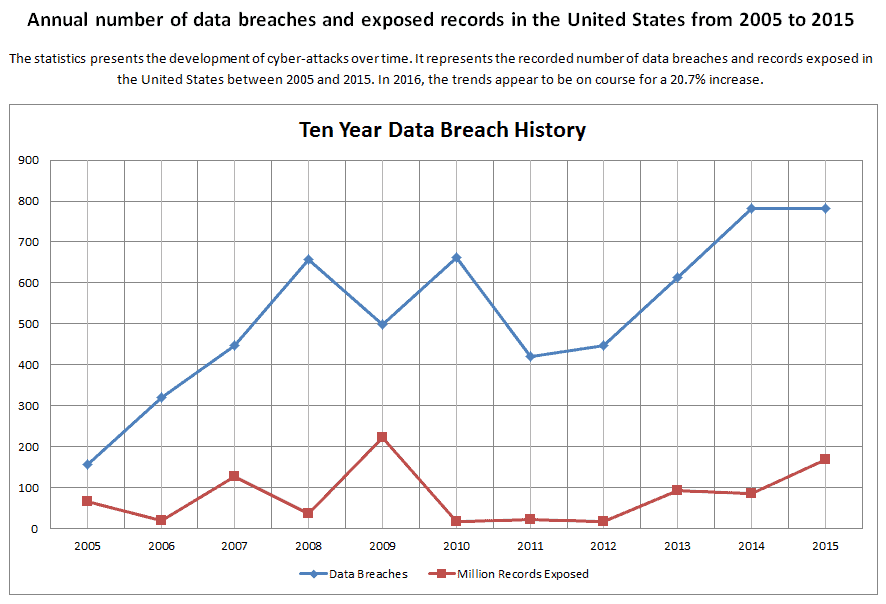
When the majority of cyber threats are waged against the SMB space and a whopping 60% of those companies will be out of business within six (6) months post breach, we are understandably sympathetic to the rising level of despair company leaders and the board is suffering with.
“Are we next? That is the big question being asked more frequently now at the board level.” Said Peters
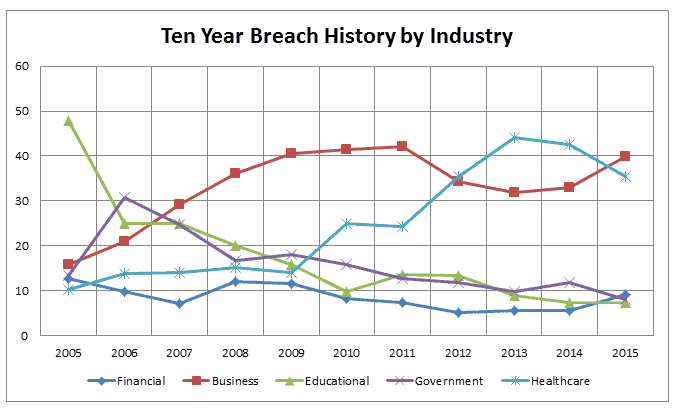
This second chart shows the percentages by industry where the cyber security data breach threats are being most successful.
NIST regulations are complex and expertise in deciphering this regulatory mystery is in short supply which is one reason ITAM IT audit software is such a great solution. Continuum GRC removed the guesswork from compliance completely. With intuitive and guided questionnaires you cannot make mistakes and missteps putting your company at risk.
Gone are the days where audits, assessments and compliance work was overshadowed by endless spreadsheets, version control madness, escalating costs and audit anarchy. The IT Audit Machine puts the power of technology, collaboration and simplicity to work for the entire enterprise and does it in a progressive, proactive way.
Cyber-crime prevention is of paramount concern to organizations of all sizes, all industries and on all parts of the world. Continuum GRC put its extensive experience in cybercrime and fraud prevention in the governance, risk and compliance (GRC) spaces to work for the global business community.
“Service providers globally are under increasing attack by cyber criminals. These criminal acts could have been prevented through a proactive cyber security position. Continuum GRC is proactive cyber security with our NIST compliance and assessment automation modules and templates.” said Peters.
Continuum GRC’s primary purpose is to help organizations attain, maintain, and demonstrate compliance and information security excellence, in any jurisdiction. Continuum GRC specializes in IT security, risk, privacy, governance, cyberspace law and compliance leadership solutions and is fully dedicated to global success in these disciplines.
Learn more about Continuum GRC and why Continuum GRC is Proactive Cyber Security™!
Download the whitepaper!
Have a question or want to schedule some time with our Superheroes?
[bpscheduler_booking_form]